Workshop: Get started with security for your Java Microservices application¶
As a developer you should ask yourself: "How can I make my application (more) secure?"
In this workshop you will learn how to get started with Application Security from two perspectives:
- Platform security
- Authentication and Authorization implementation
We will show you with an example application:
- How to secure external access to a Kubernetes cluster with TLS
- How to secure communication between Microservices with Istio and mTLS
- How to implement authorization and authentication with the Open Source Identity and Access Management system Keycloak and JSON Web Tokens (JWT)
The exercises are based on an example application based on our Open Source Github project Cloud Native Starter, build with Quarkus and Microprofile
The following screenshot shows the web application, you have to logon to see the list of articles.
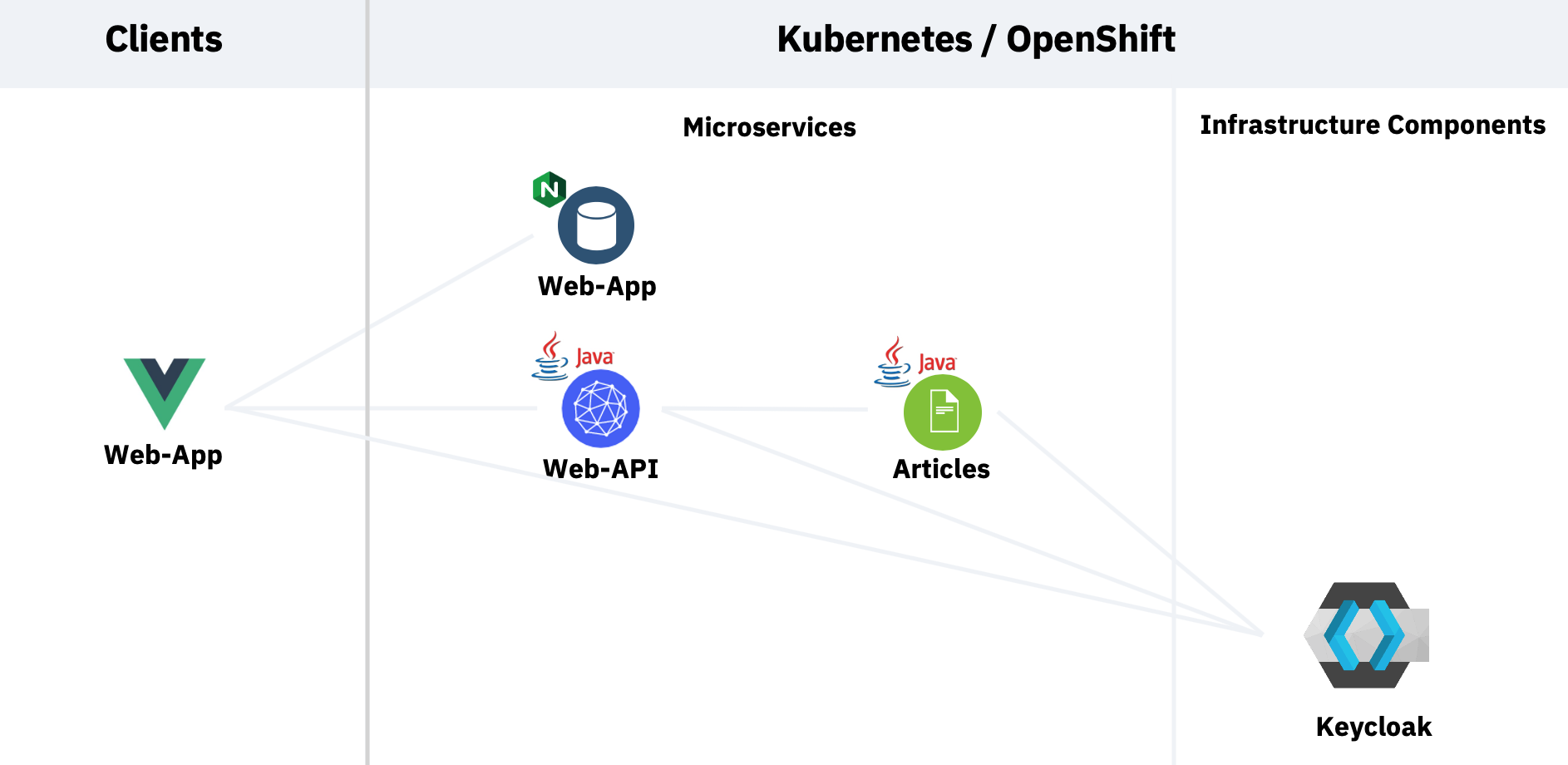
Architecture¶
The following diagram shows the architecture of the sample application. There is a Web-App service that serves the Javascript/Vue.js code to the browser. The Web-App code running in the browser invokes a REST API of the Web-API microservice. The Web-API microservice in turn invokes a REST API of the Articles microservice.
To see the results in the web application, users need to be authenticated and they need to have the role user.
Estimated time and level¶
| Time | Level |
|---|---|
| one hour | beginners |
Objectives¶
After you complete this workshop, you'll understand the following application security related topics:
Application security provided by the platform
Application security with Keycloak and Quarkus
- Authentication with Keycloak on the Web Fronted
- Authorization in Quarkus for specific Microservices in the backend
The scope of this workshop is not to explain every aspect of application security.
About this workshop¶
Agenda¶
These are the sections of this workshop, go through all of them in sequence, start with 1. Setup the IBM Cloud Environment :
- Setup the IBM Cloud Environment
- Setup the IBM Cloud application environment
- Platform security with mTLS
- Application security with Keycloak and Quarkus
Compatibility¶
The workshop with his two major parts, has been tested on the following platforms and local installations:
-
Platform security
- IBM Cloud Kubernetes Service: Kubernetes Version 1.17, Istio Version 1.5 on IBM Cloud (pre-provisioned for the workshop or a paid cluster)
- IBM Cloud Shell: Version 1.0.2
-
Authorization and authentication implementation
- git 2.24.1
- yarn 1.22.4
- Node.js v14.6.0
- Apache Maven 3.6.3
- Docker 3.0.4
- Java 9
Technology Used¶
- Microservices architecture
- KEYCLOAK
- Jakarta EE
- MicroProfile
- Quarkus
- Ingress
- Istio
- Vue.js
- NGINX
- Kubernetes
- git 2.24.1 or higher
- yarn 1.22.4 or higher
- Node.js v14.6.0 or higher
- Apache Maven 3.6.3
Credits¶
Additional resources¶
Here are some blogs that describe how this project has been implemented-
The presentation that goes with this workshop is available here.