Create DevSecOps pipelines to update a Kubernetes application¶
DevSecOps integrates a set of security and compliance controls into the DevOps processes, allowing frequent code delivery while maintaining a strong security posture and continuous state of audit-readiness.
This setion steps you through the creation of Continuous Integration (CI) toolchains using an IBM Cloud toolchain templates, which we will customize to deploy the sample application to an IBM Cloud Kuberenets cluster.
Before you begin¶
Set up the following pre-requisites:
-
Ensure you have cloned the following repos to your GitHub account:
-
https://github.com/IBM/multi-tenancy
- https://github.com/IBM/multi-tenancy-backend
-
https://github.com/IBM/multi-tenancy-frontend
-
An instance of the IBM Cloud Secrets Manager service
- An IBM Cloud Kubernetes Service cluster or an IBM Cloud OpenShift cluster
- Create a namespace in the IBM Cloud Container Registry (access via hamburger menu->Container Registry)
- Create Postgres and AppId service instances, and service API keys. See section Creation of managed IBM Cloud Services
Create an IBM Cloud API key in Secrets Manager¶
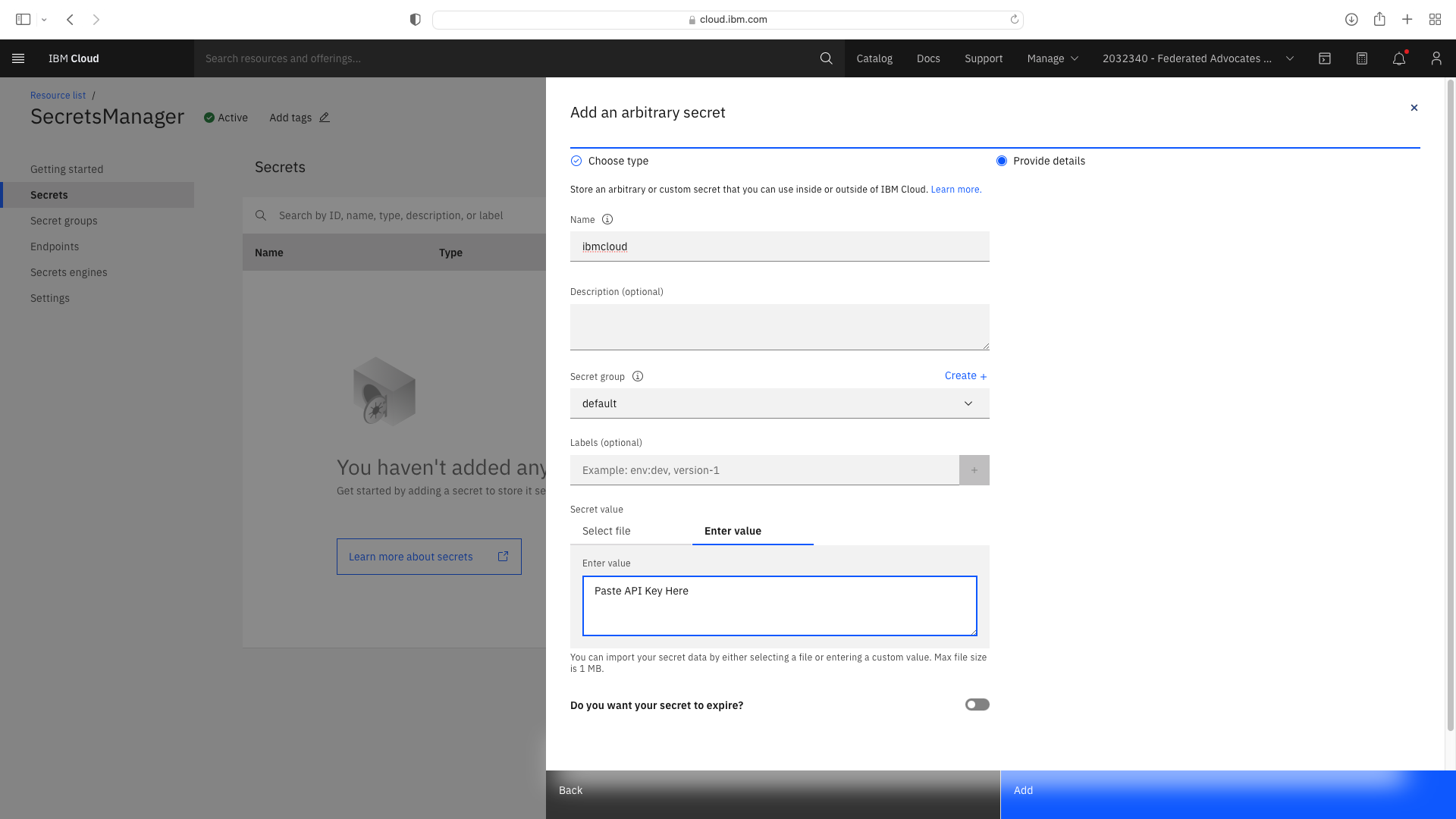
In IBM Cloud, navigate to Manage->Access (IAM)->API Keys. Create a new IBM Cloud API Key and make a note of it.
In your Secrets Manager service, create a new Arbitary value and paste in the IBM Cloud API Key:
Update the sample application configuration¶
In your clone of https://github.com/IBM/multi-tenancy, navigate to the folder configuration/tenants. This is the configuration file for each tenant of the SaaS application which the toolchains will deploy. You should update both tenant-a.json and tenant-b.json with the name of the IKS cluster you are using for testing, and commit the changes:
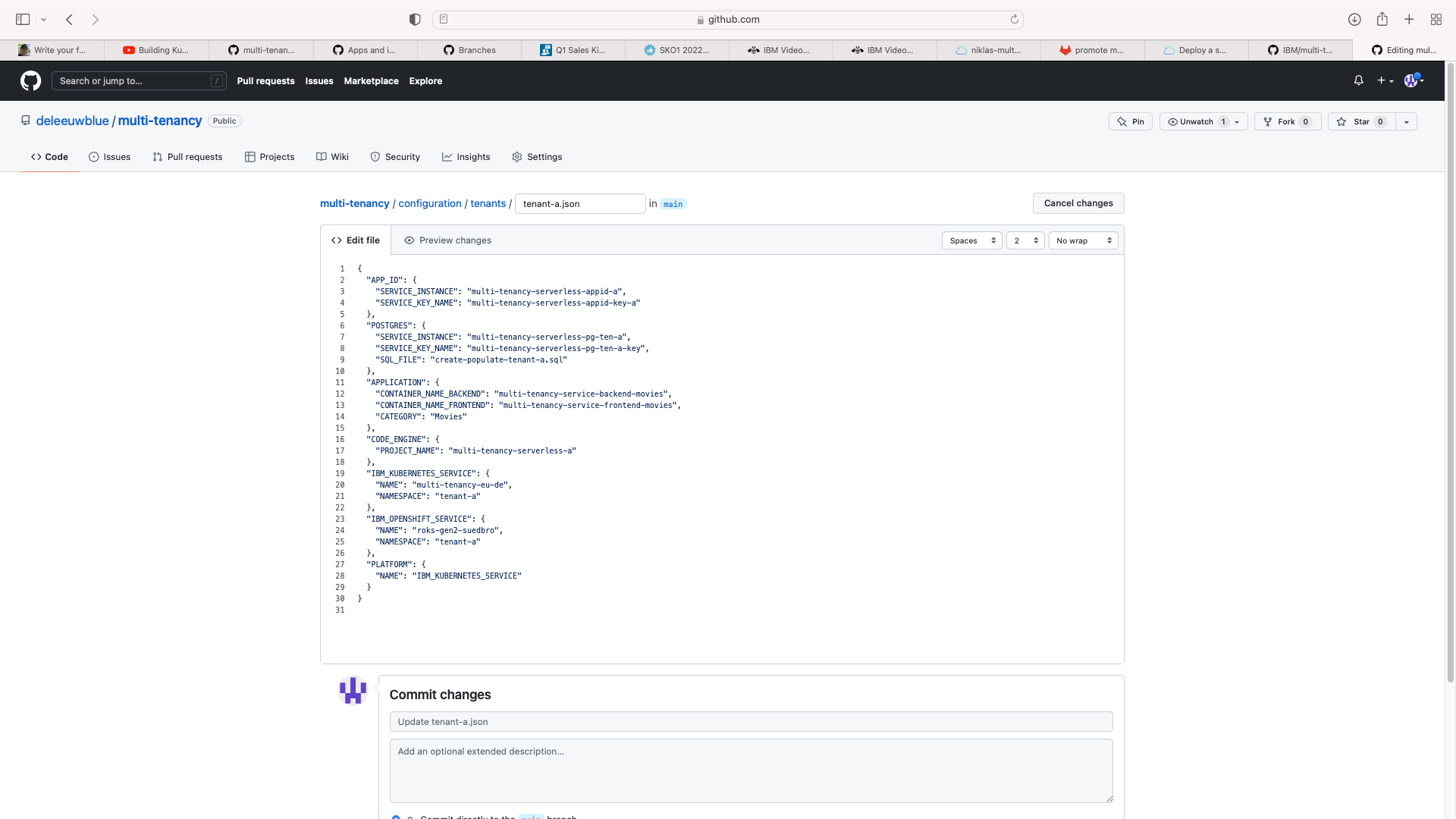
N.B. the wizard to create the toolchains (below) also requests the name of the kubernetes cluster, but the resulting toolchain environmental property is not used by this sample. Also note the definition of SERVICE_KEY_NAME fields for the AppId and Postgres cloud services. If you have previously deployed the sample code to serverless, the deployment scripts should have created appropriate API keys.
In folder configuration/global.json, update the values for the RESOURCE_GROUP and REGION where you created your Kubernetes cluster, and the container registry NAMESPACE you created for the container images:
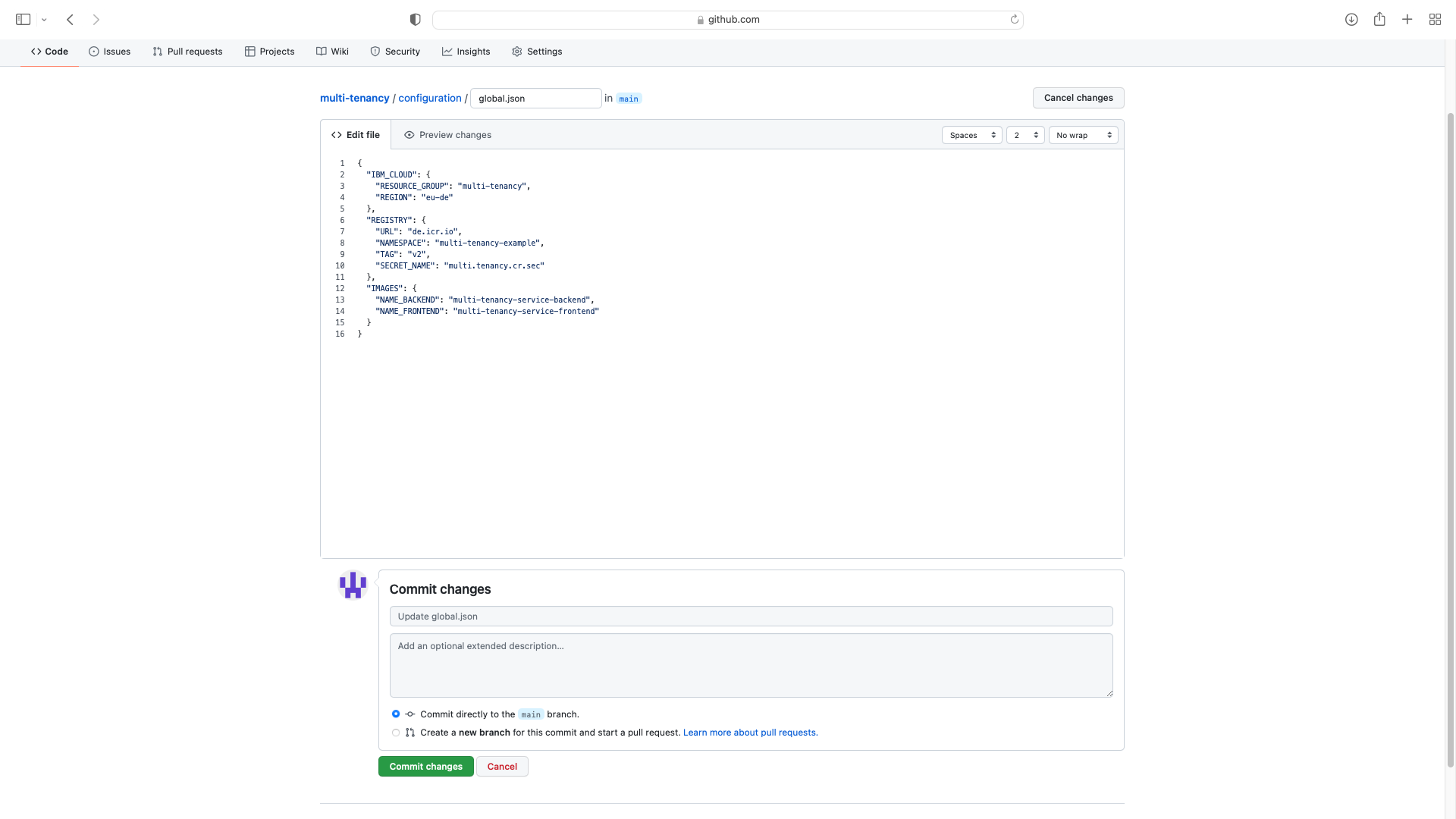
It is not necessary to change the IMAGES section.
Create the CI Backend toolchain¶
Login to IBM Cloud and use the hamburger menu in the top left to navigate to DevOps. Select the Resource Group and Region thenh Create Toolchain and select the DevSecOps filter:
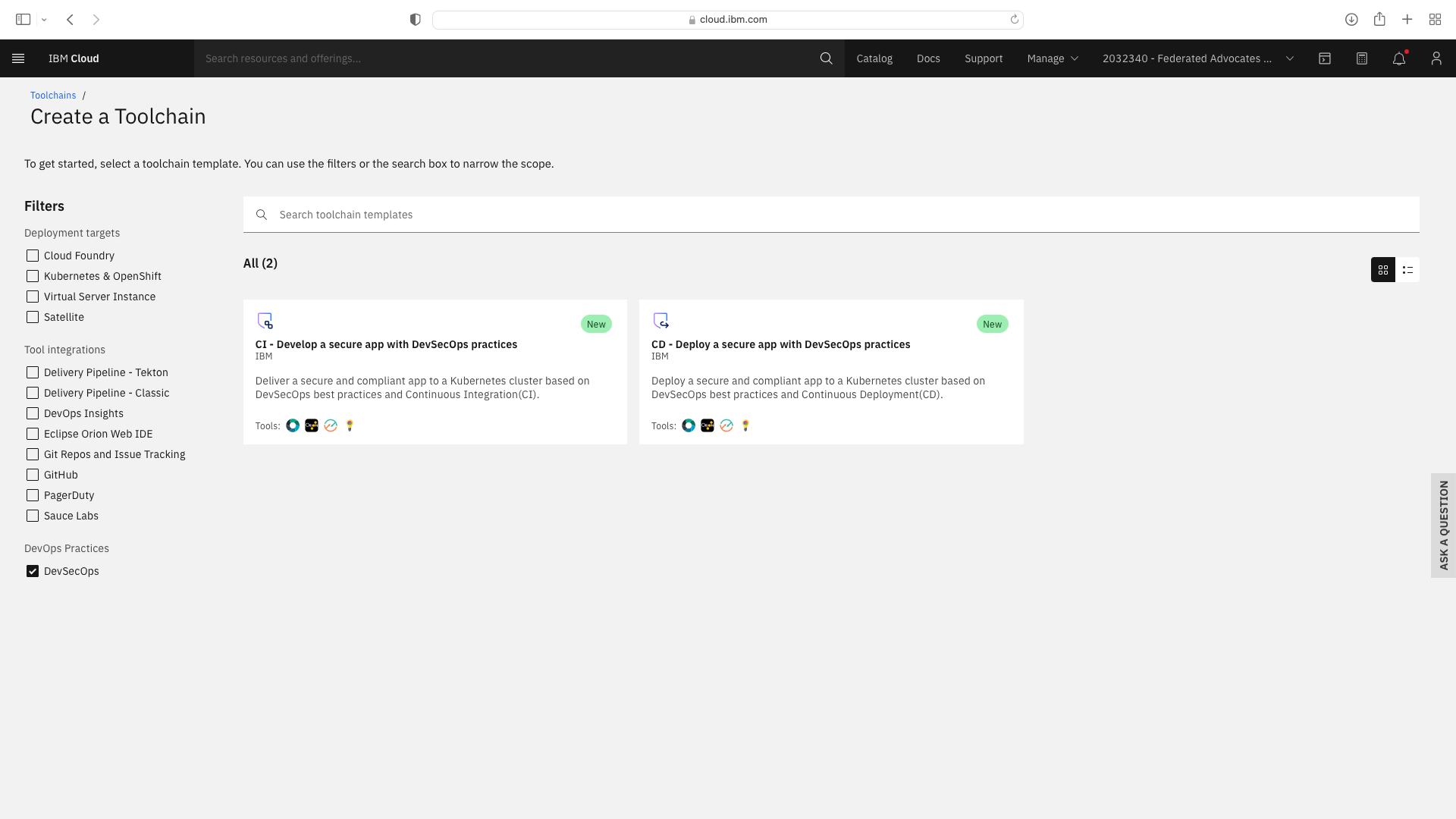
Click the CI tile to launch the setup wizard, and complete the fields by refering to the following screenshots (refering to your own GitHub repos):
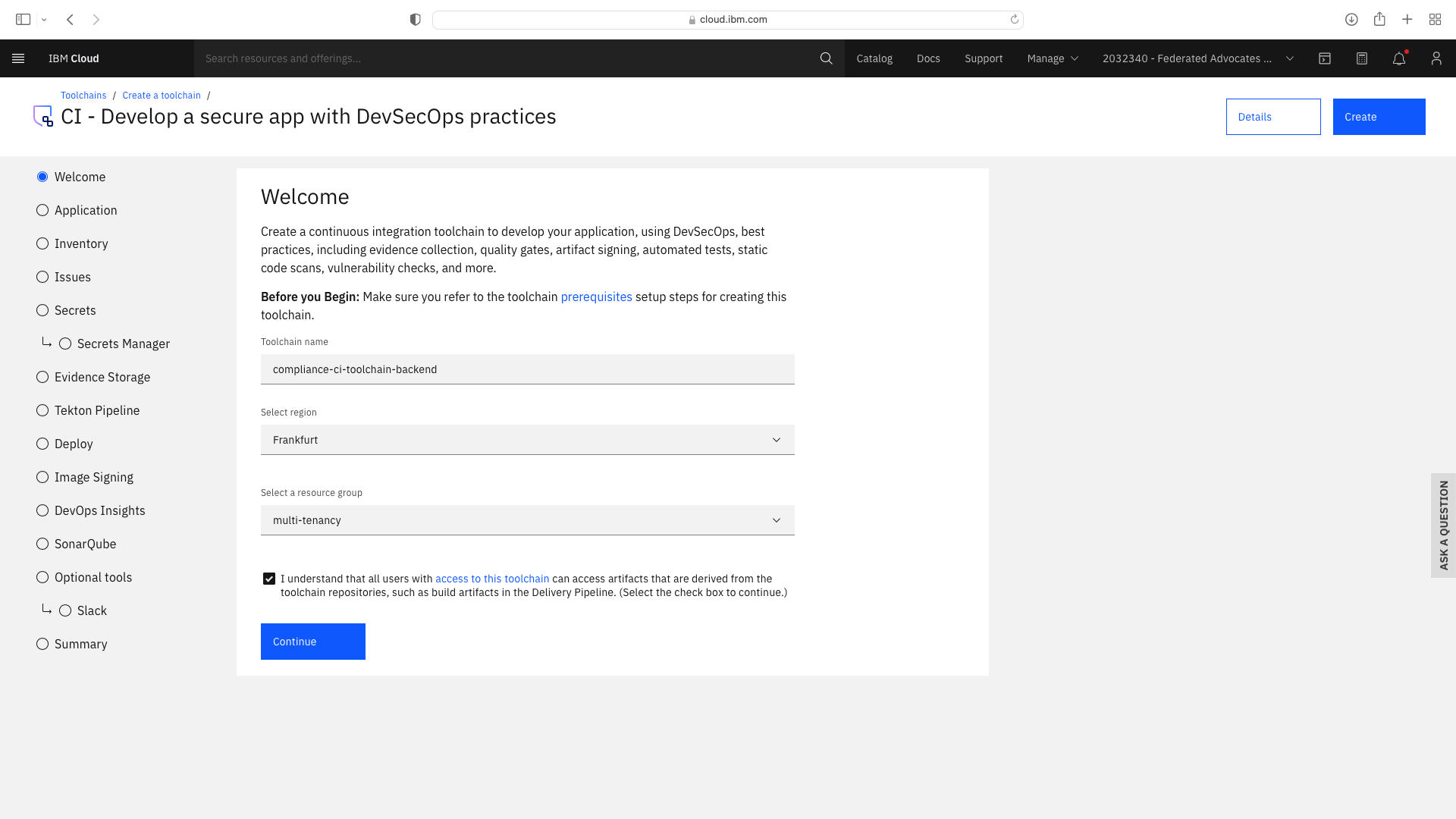
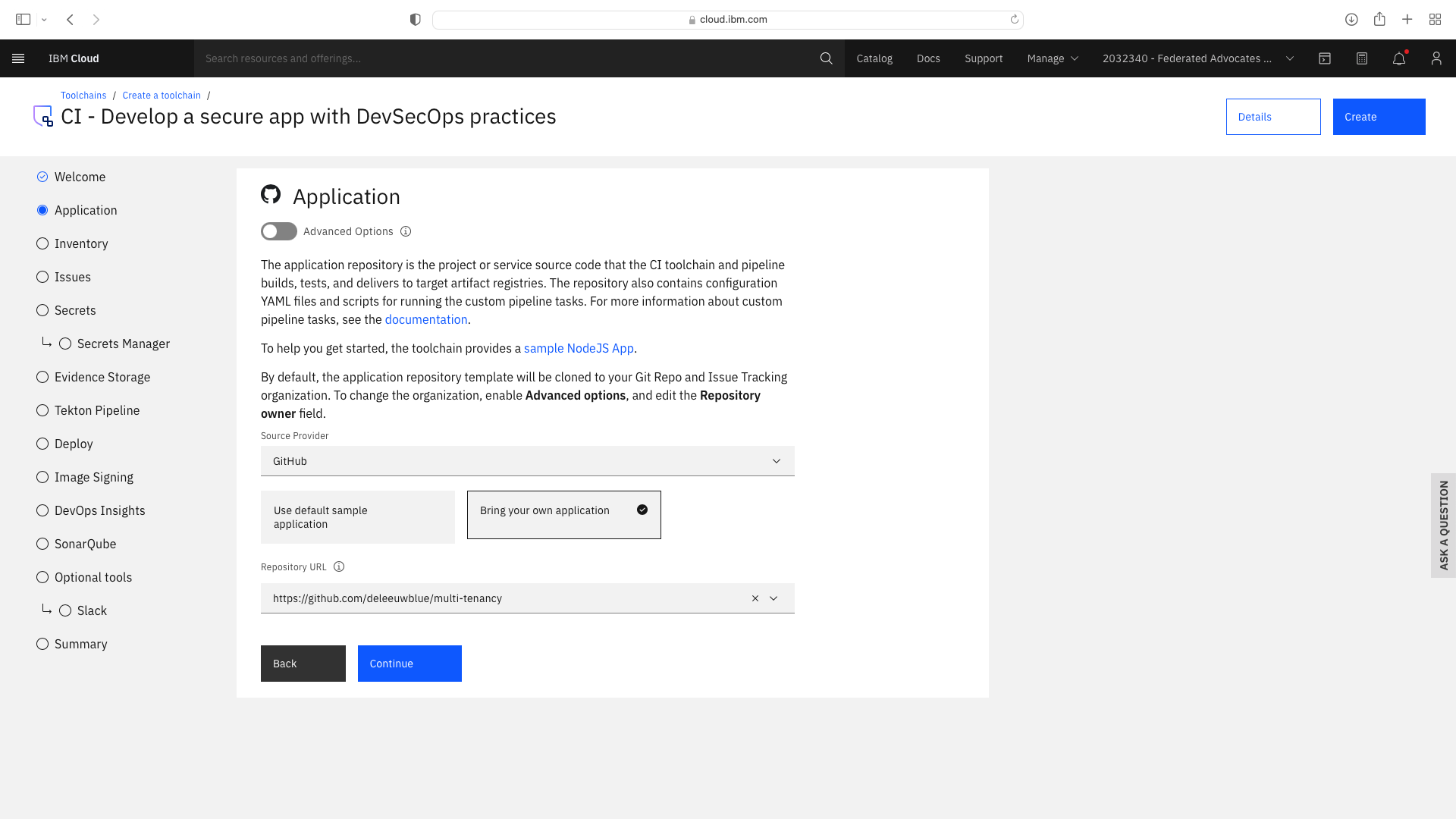
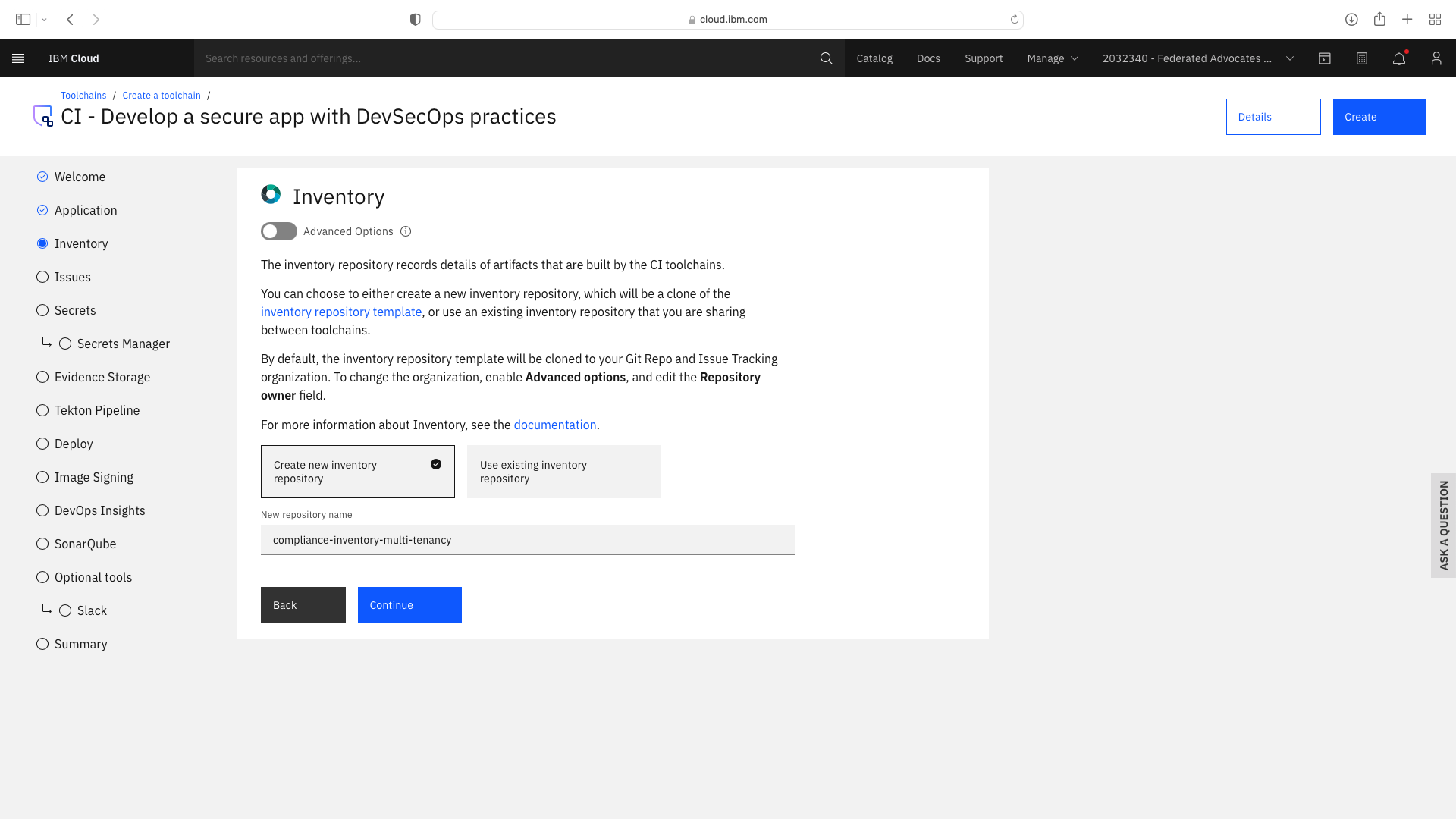
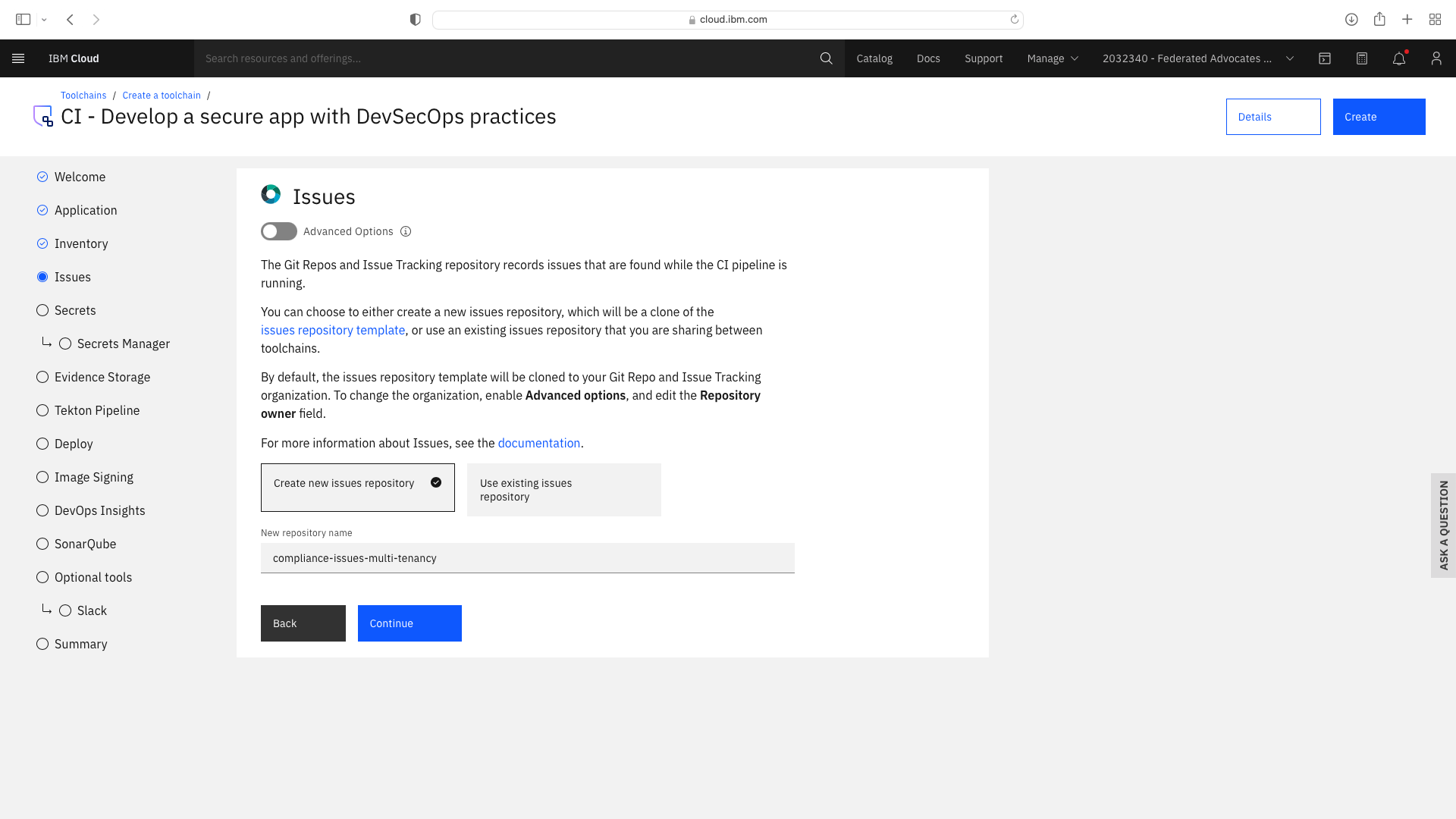
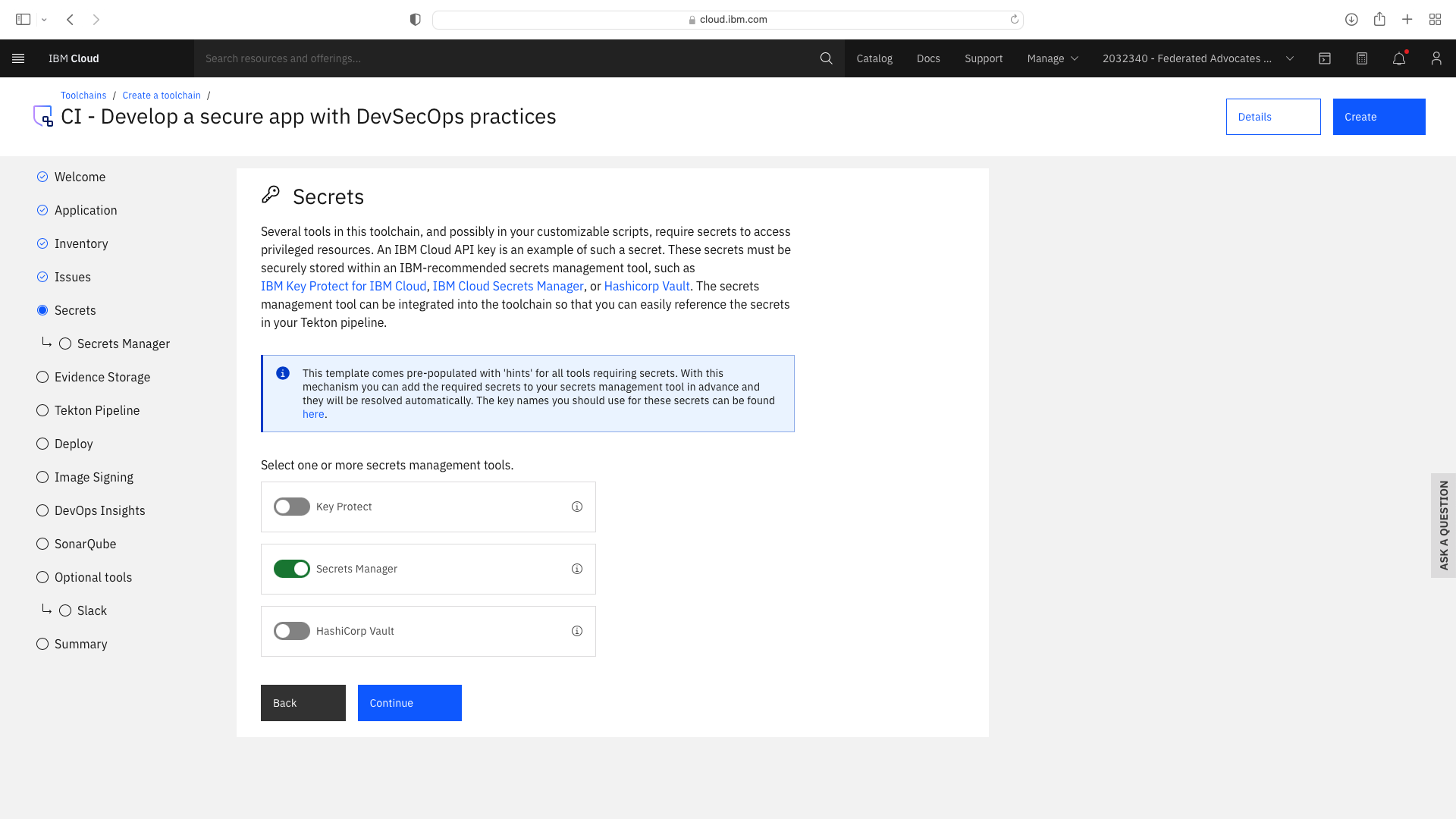
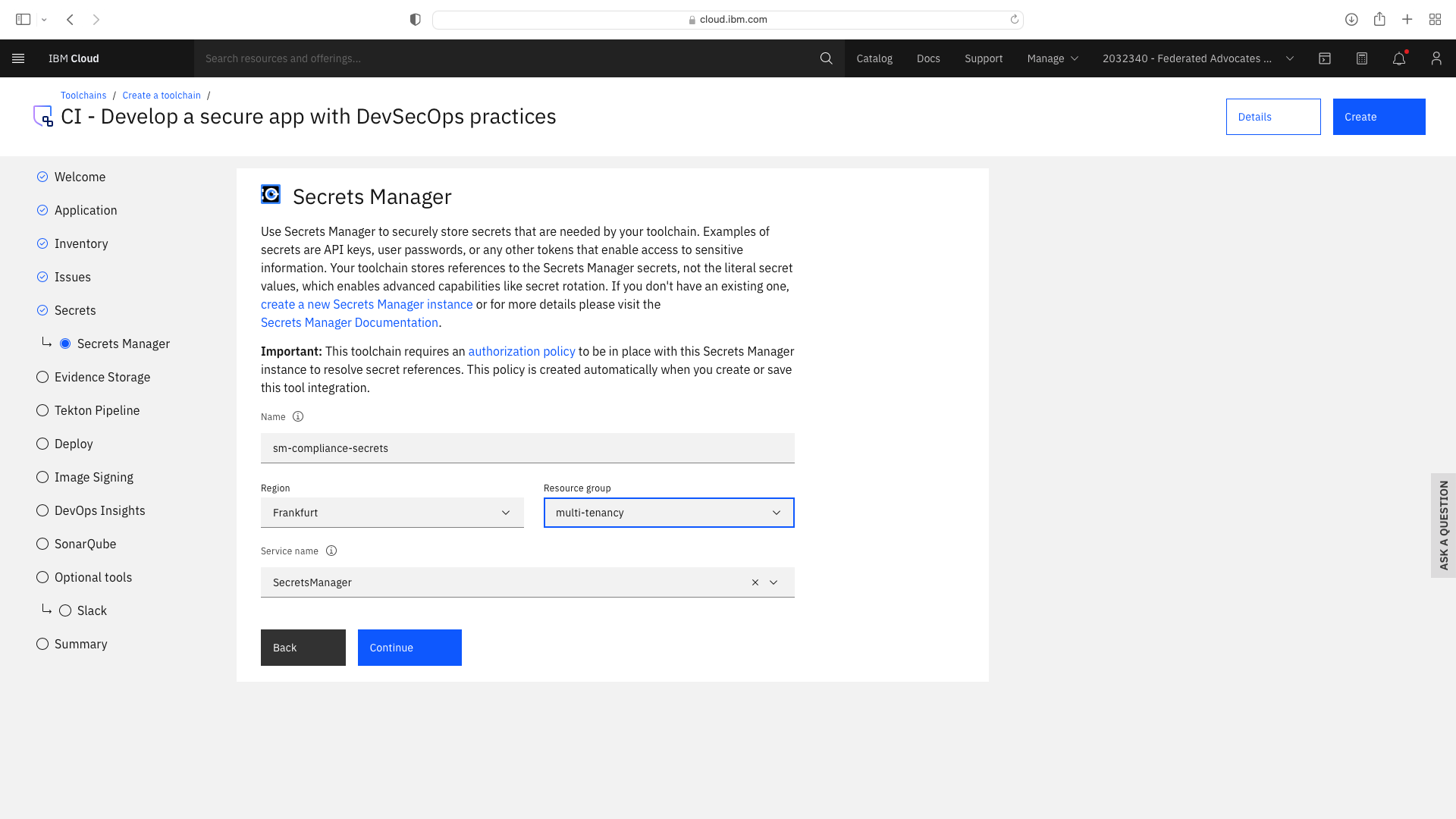
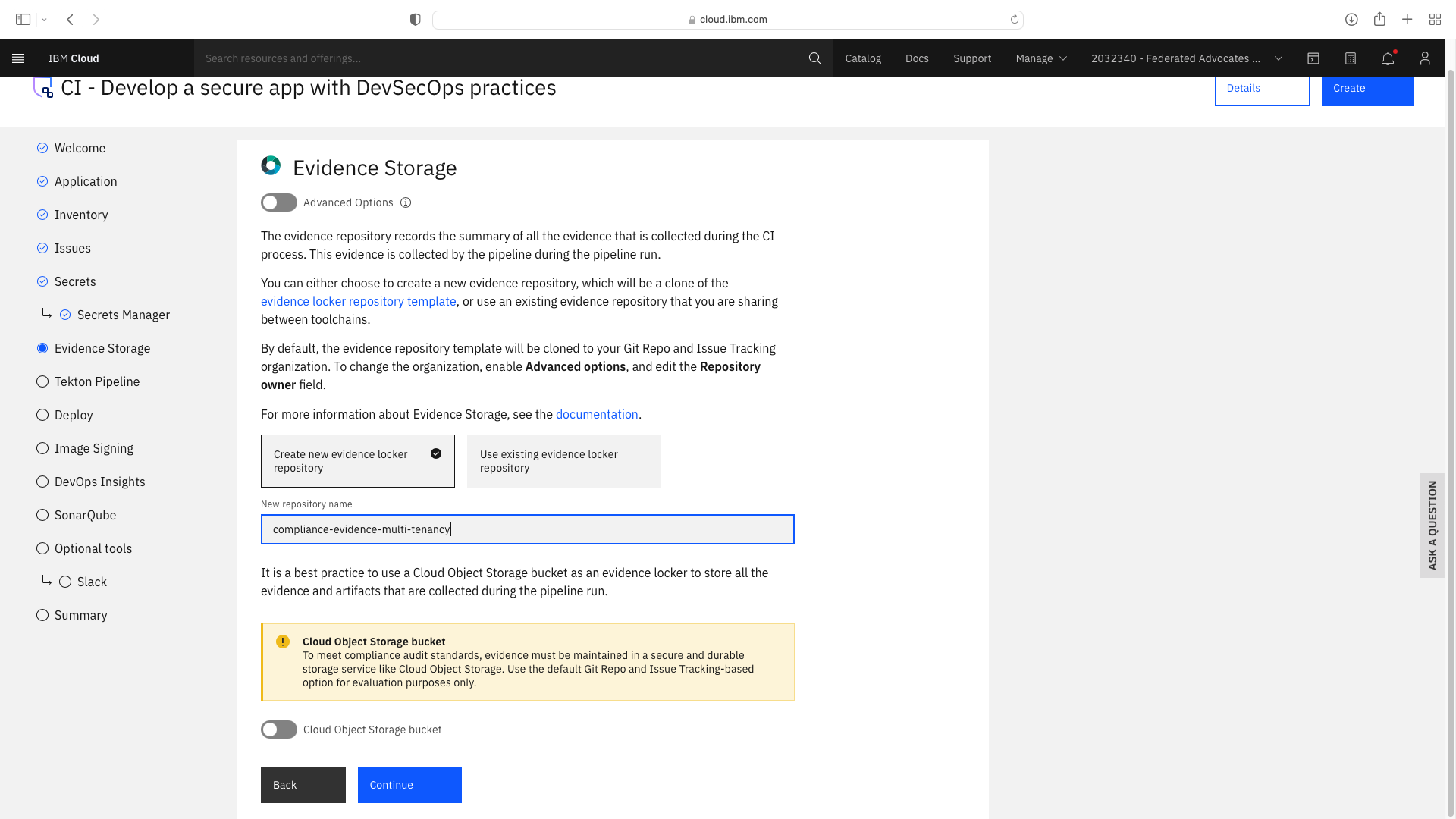
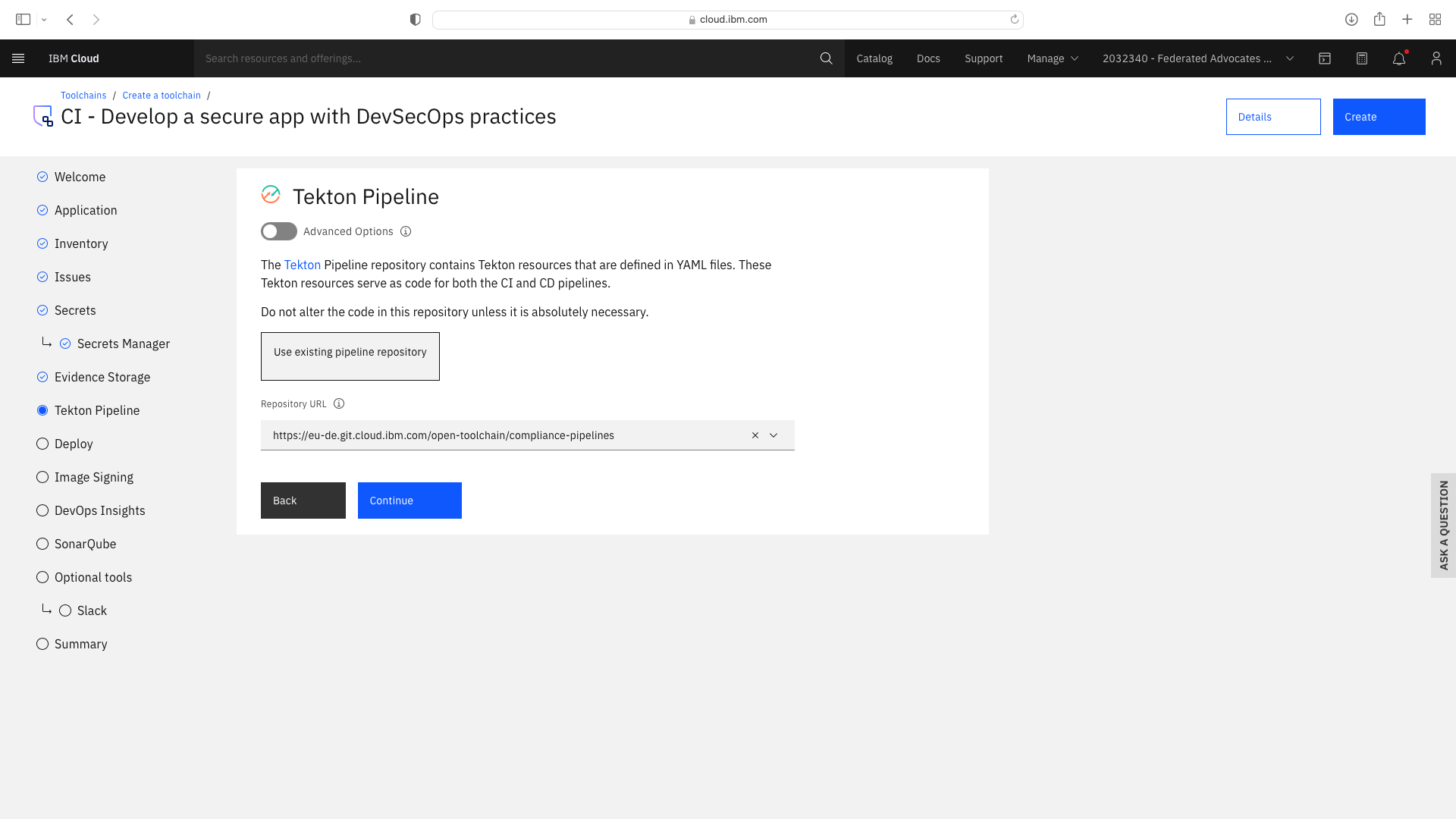
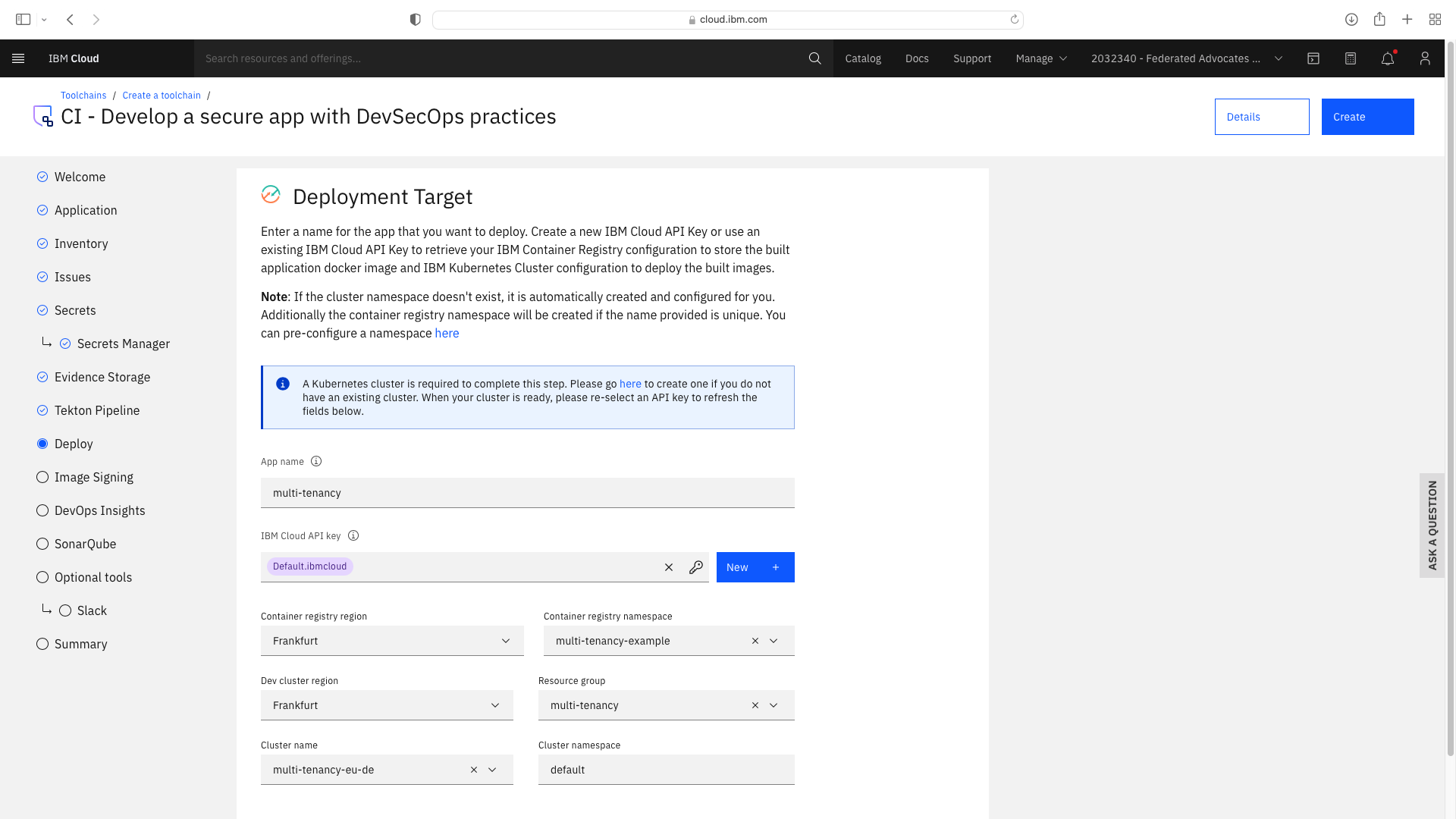
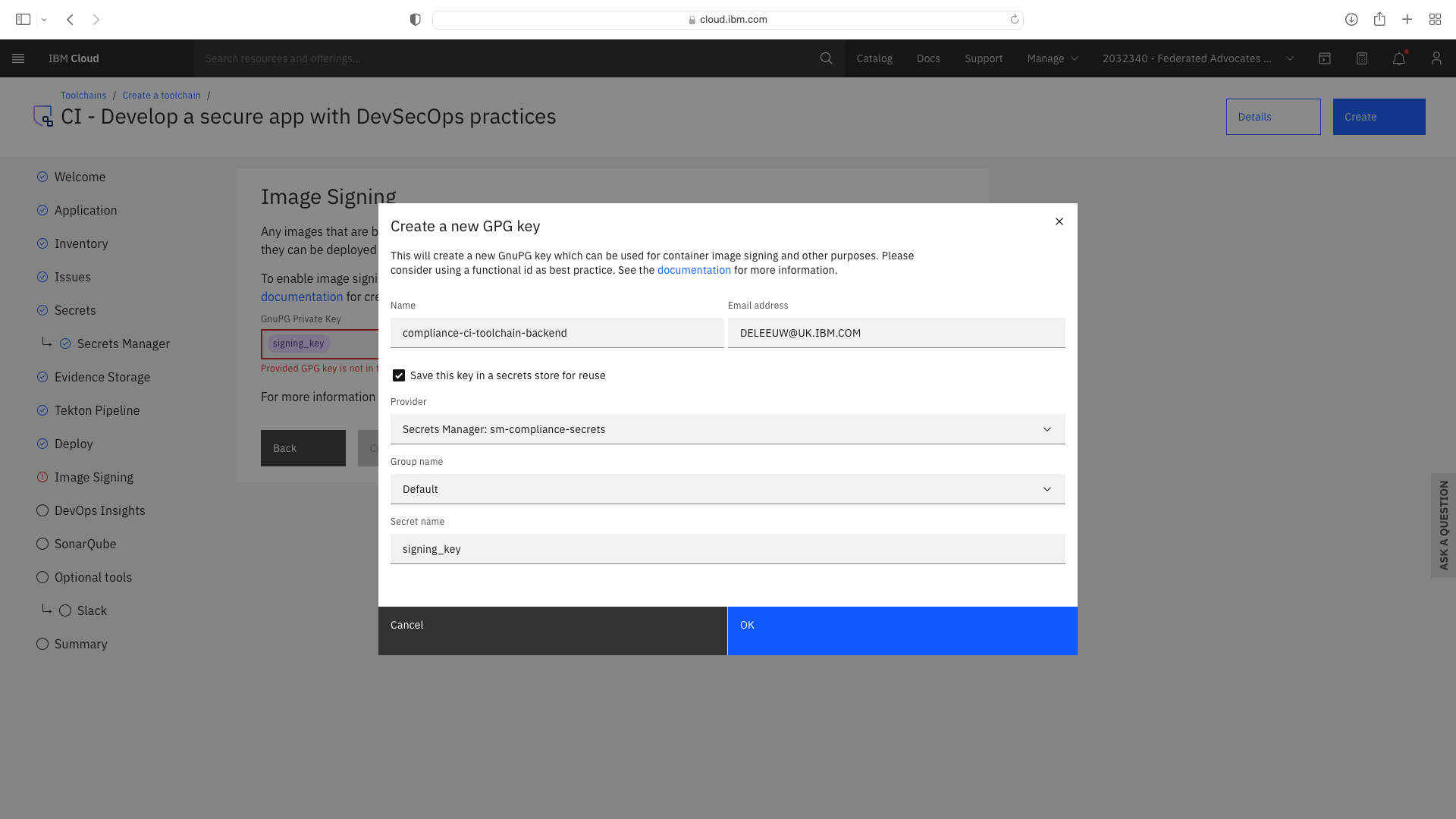
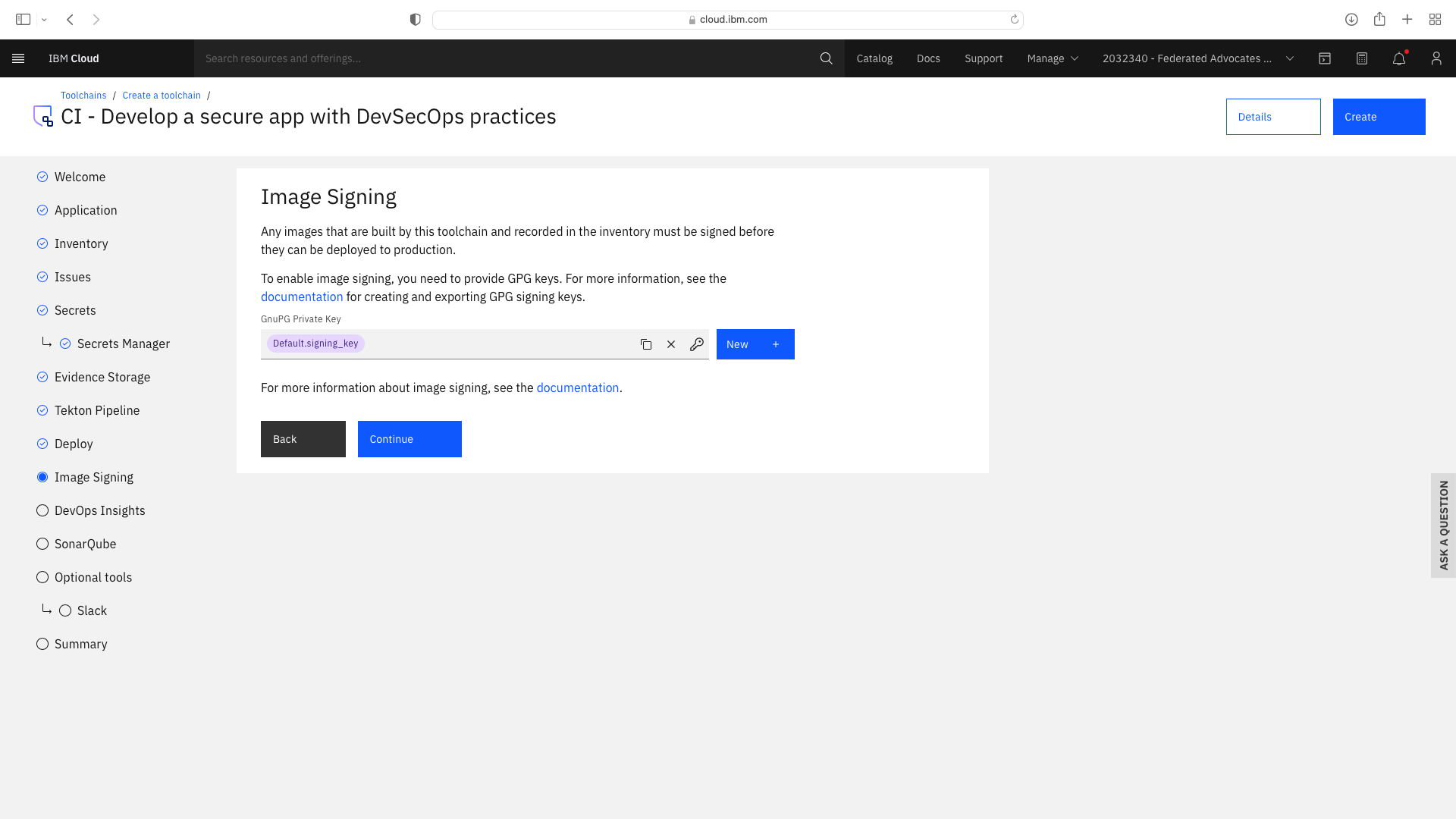
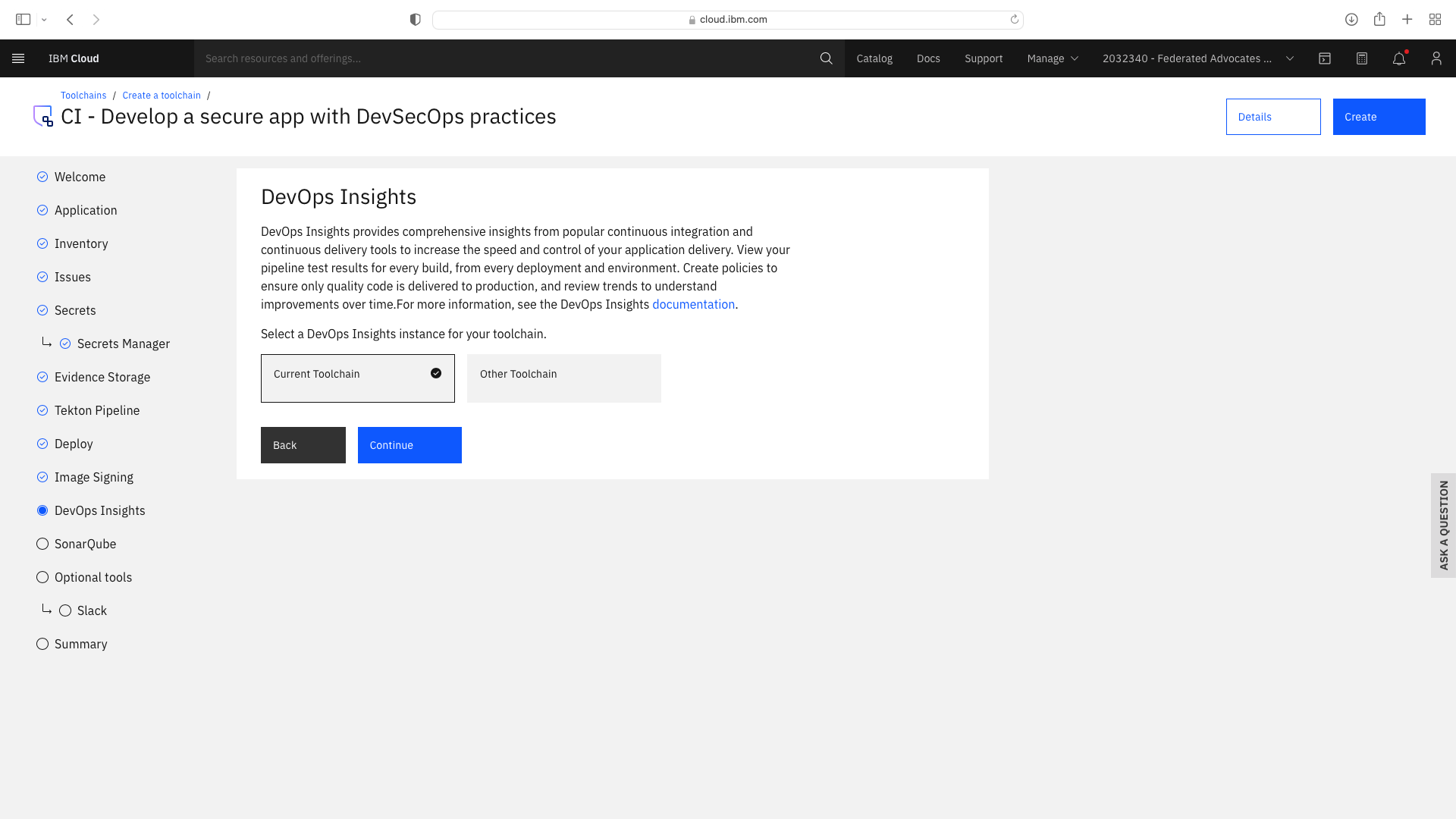
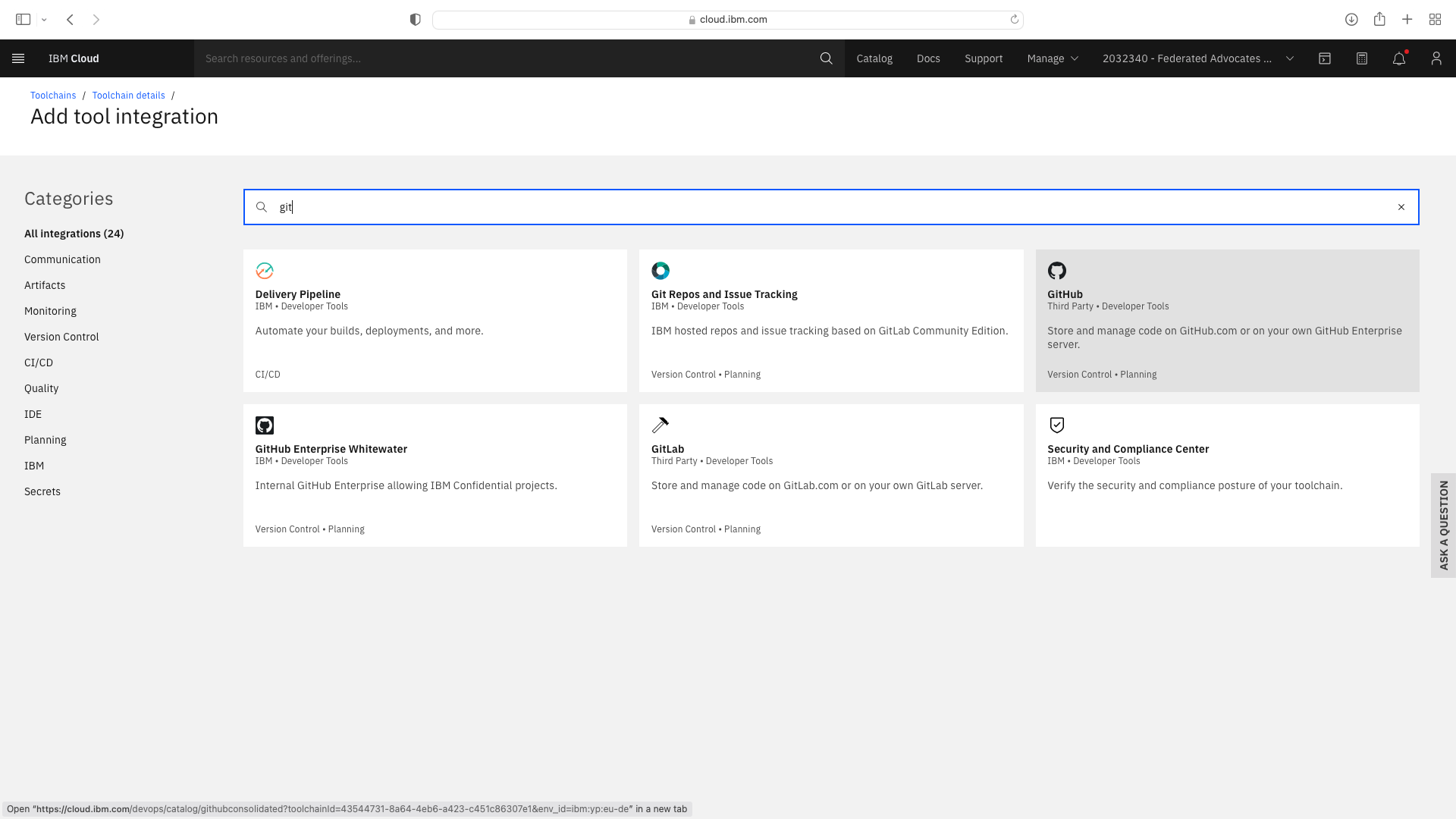
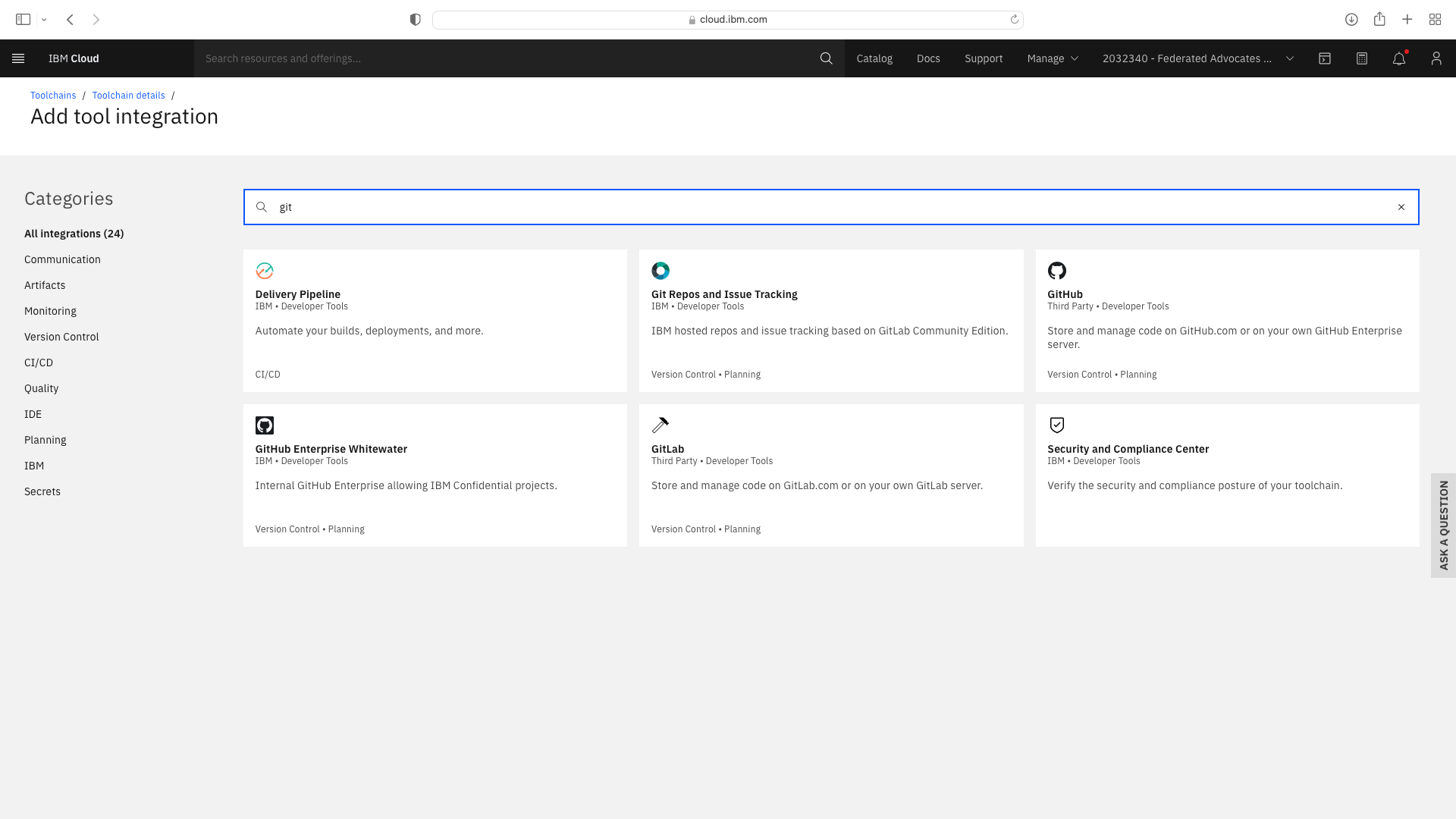
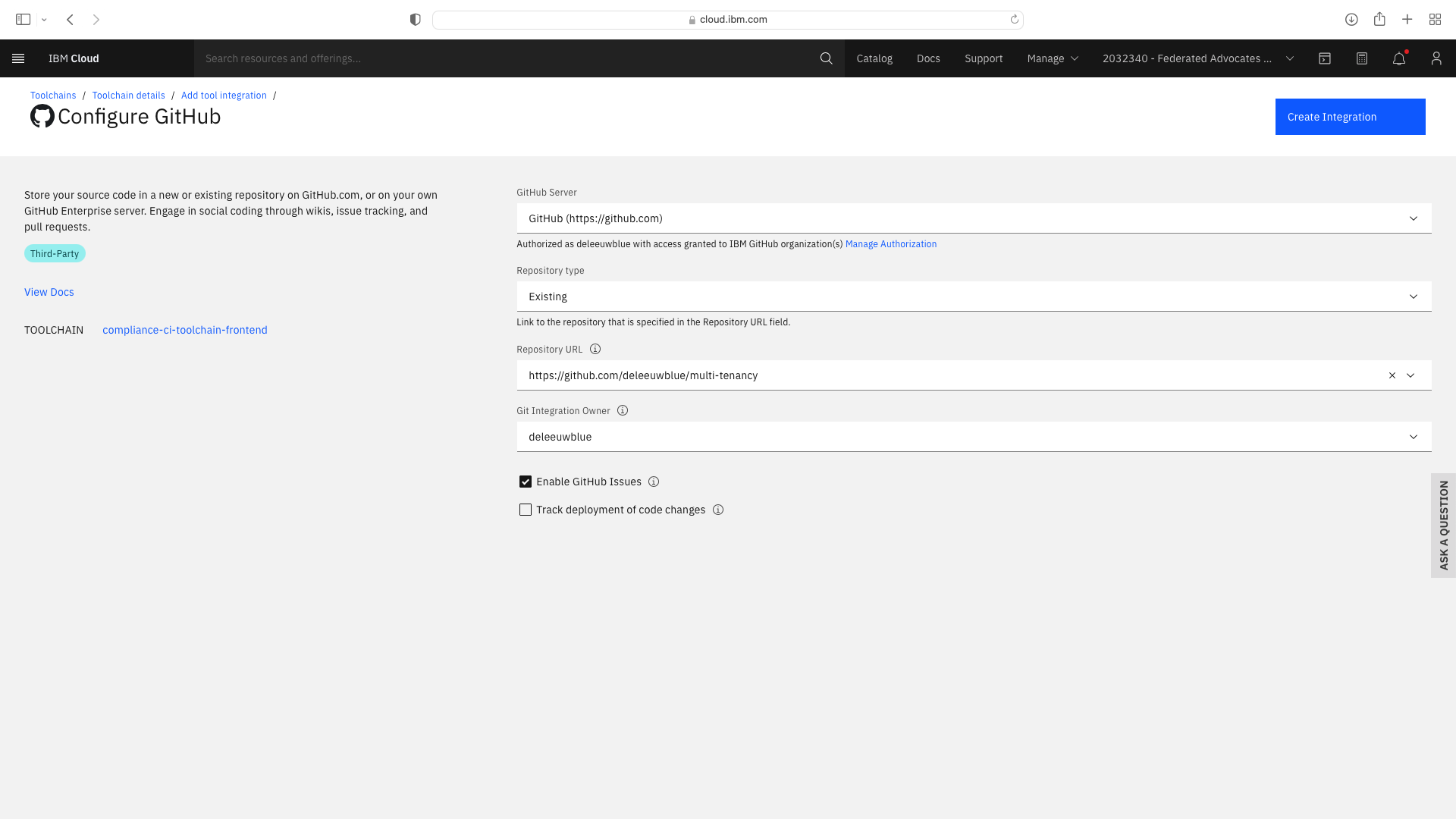
The CI pipeline for backend also requires access to the multi-tenancy repostory, in addition to the multi-tenancy-backend repostory which has already been configured by the wizard. Click the blue Add tool button and manually add the GitHub repostory for multi-tenancy by following these steps:
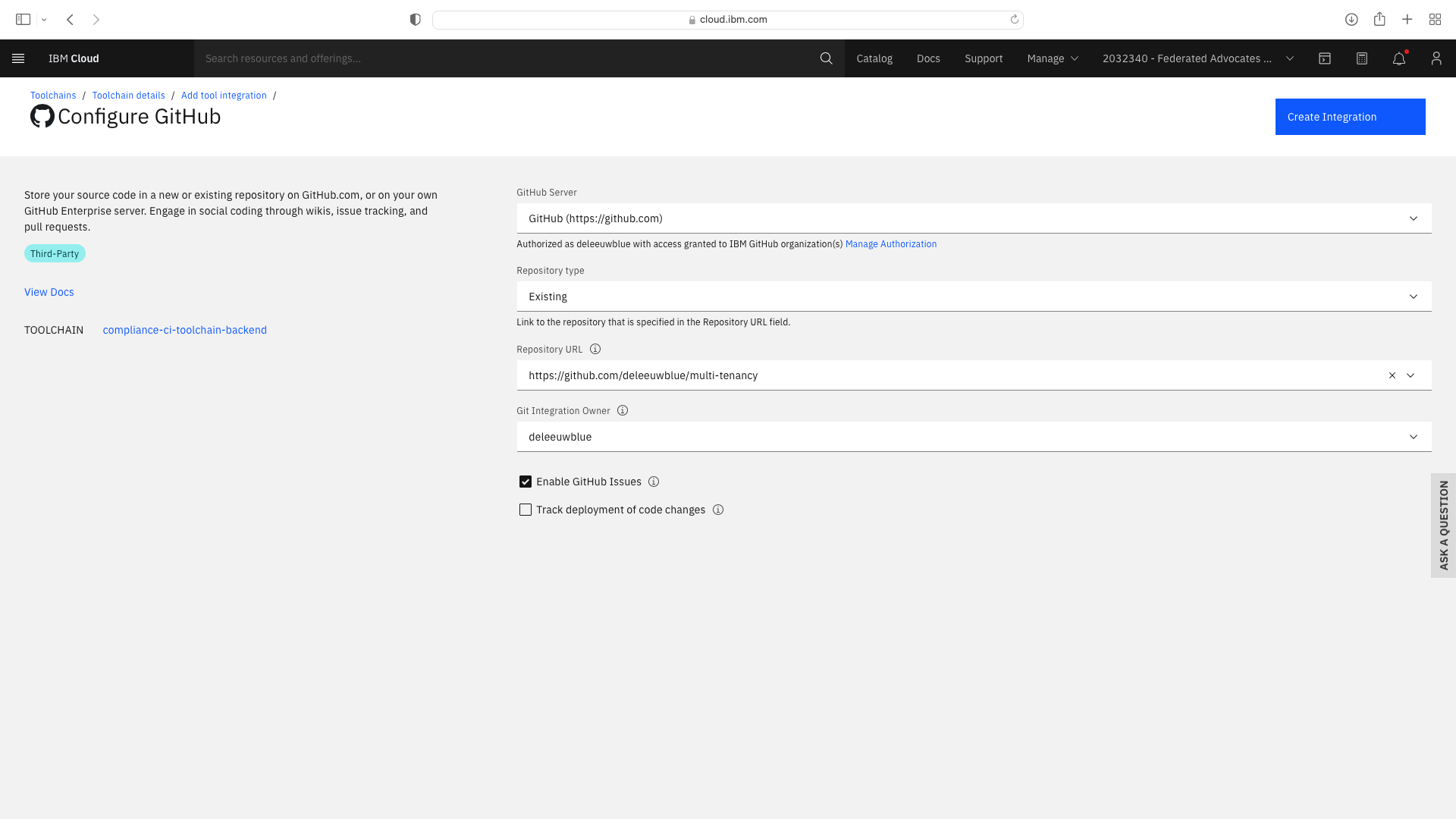
Add or update the toolchain's Environmental Properties as follows:
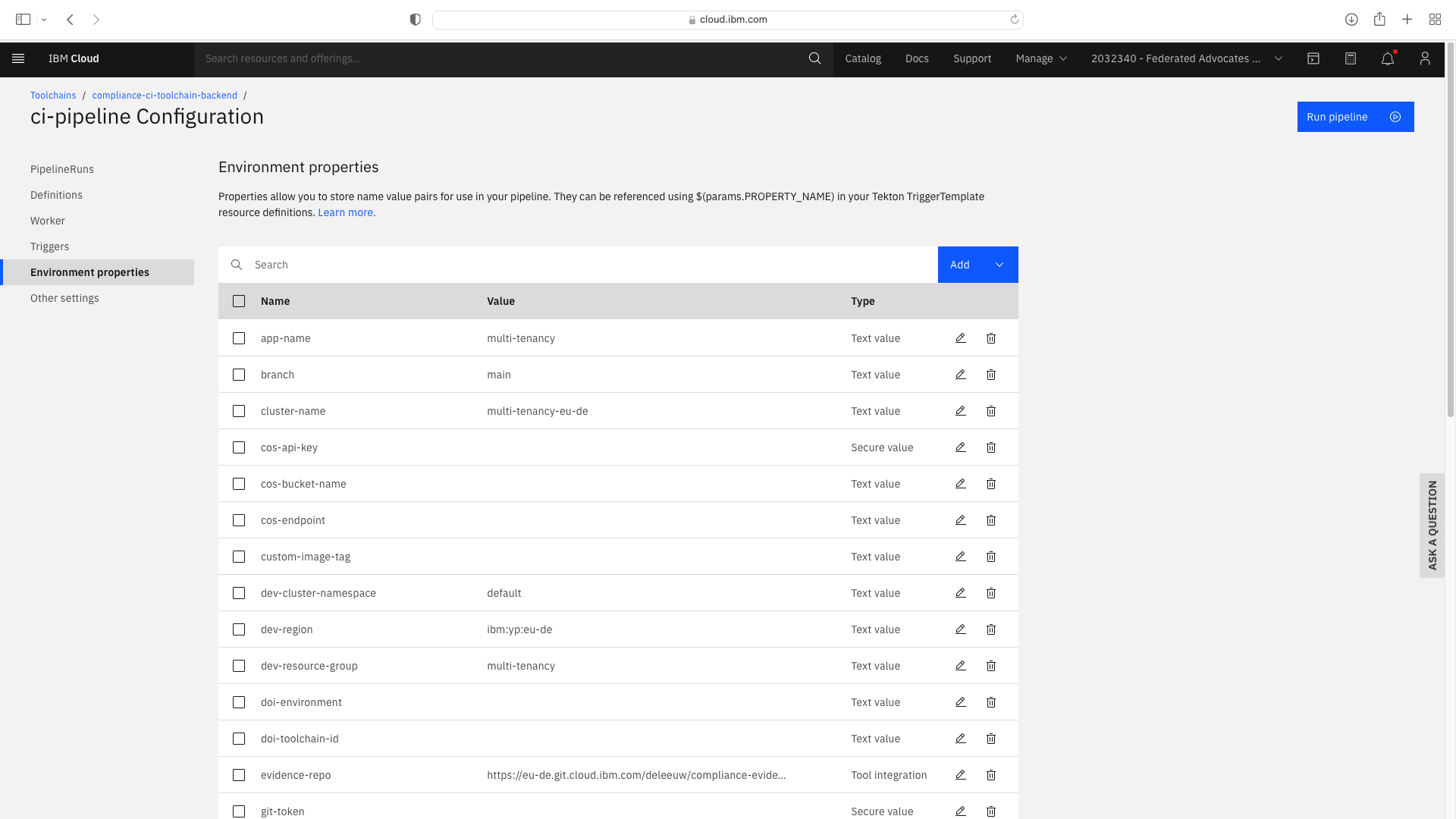
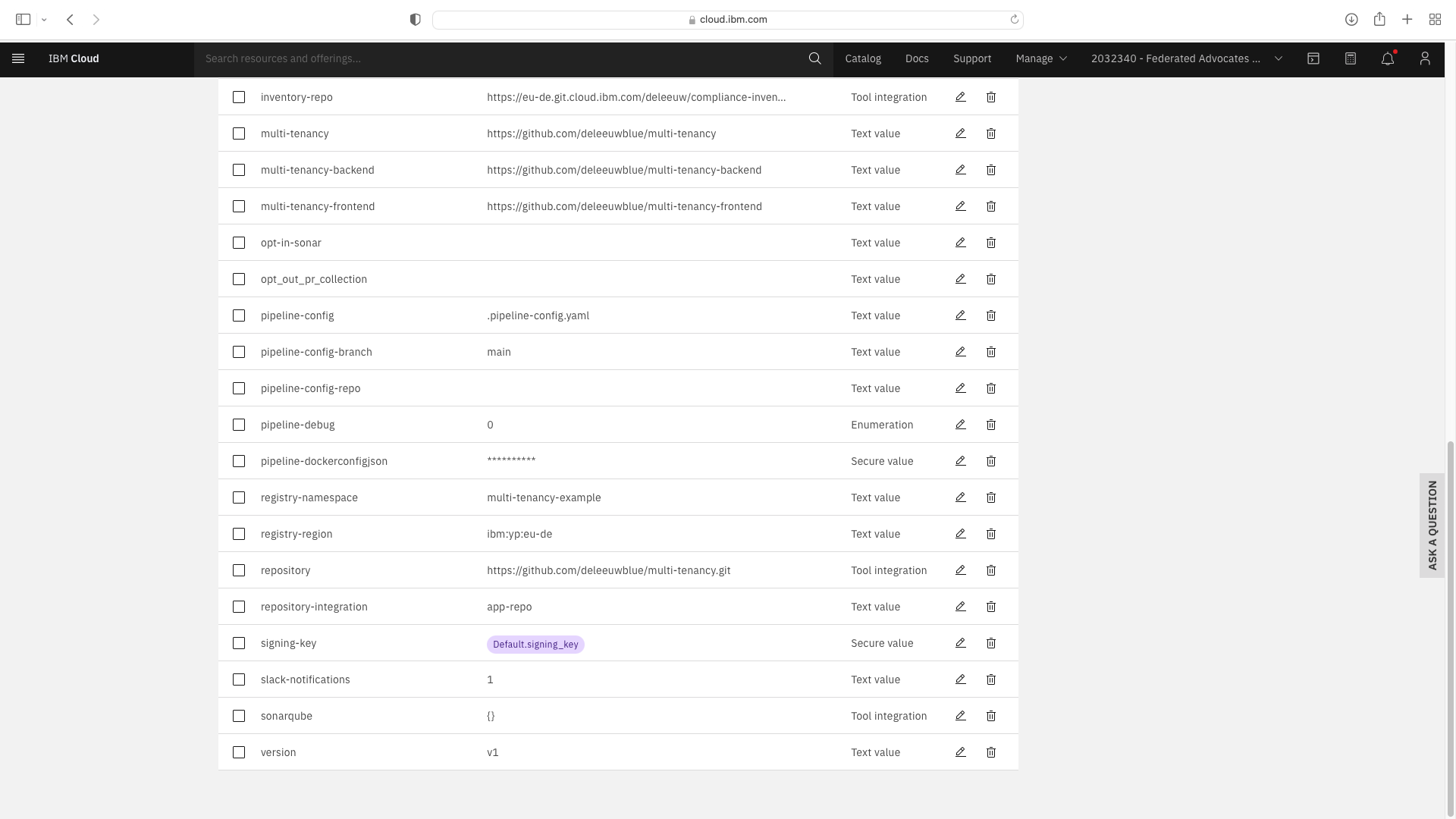
Note that the Text fields pipeline-config-branch and opt-in-sonar need to be modified.
An additional Text Fields entitled branch, multi-tenancy-frontend, multi-tenancy-backend and multi-tenancy were added.
An additional Tool Integration field entitled repository was added. When setting this field, you must specify a JSON filter of parameters.repo_url:
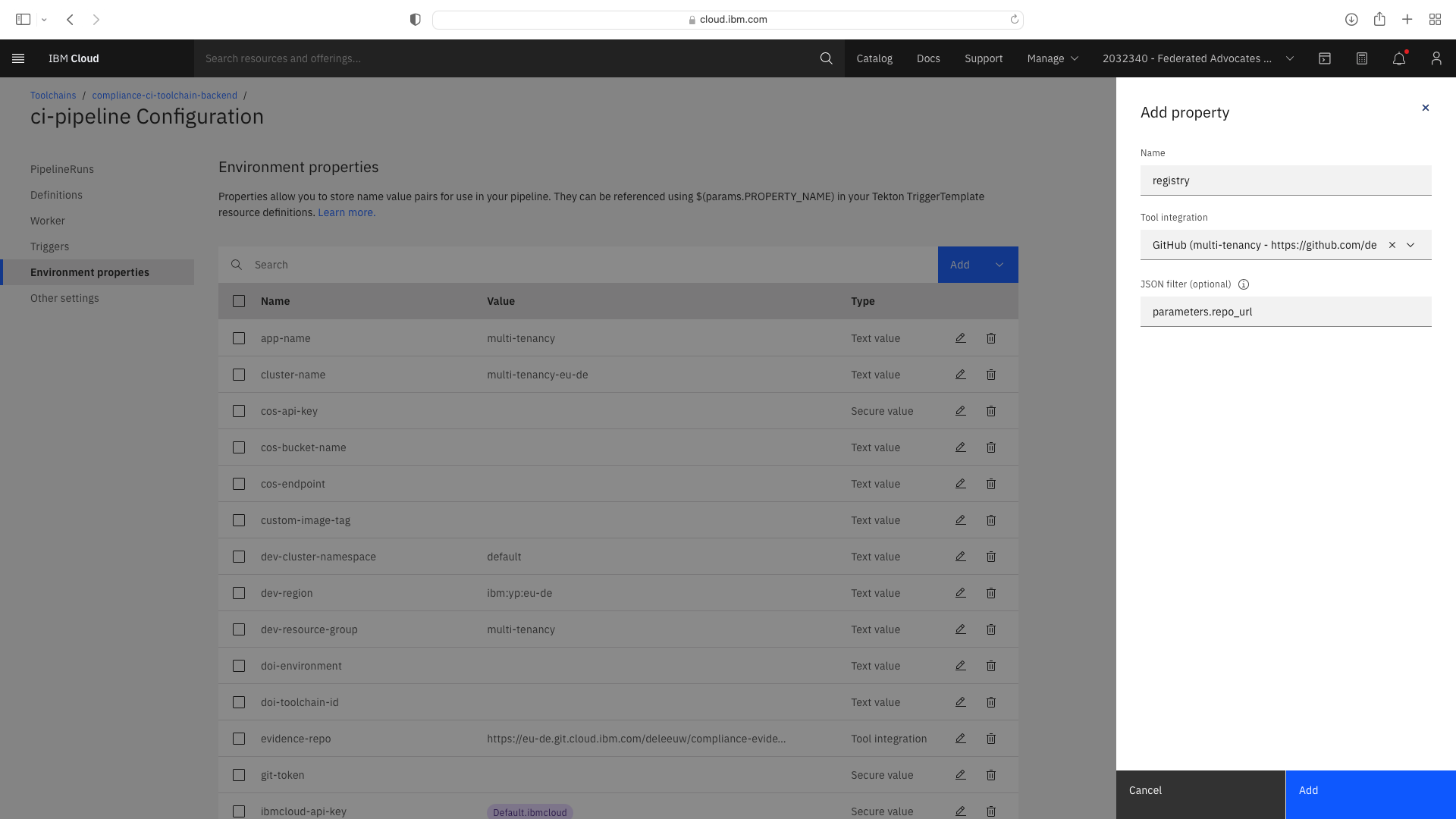
Select the Trigger tab. Note the Git CI Trigger shows a hazard symbol. Edit its properties and select a valid the branch name:
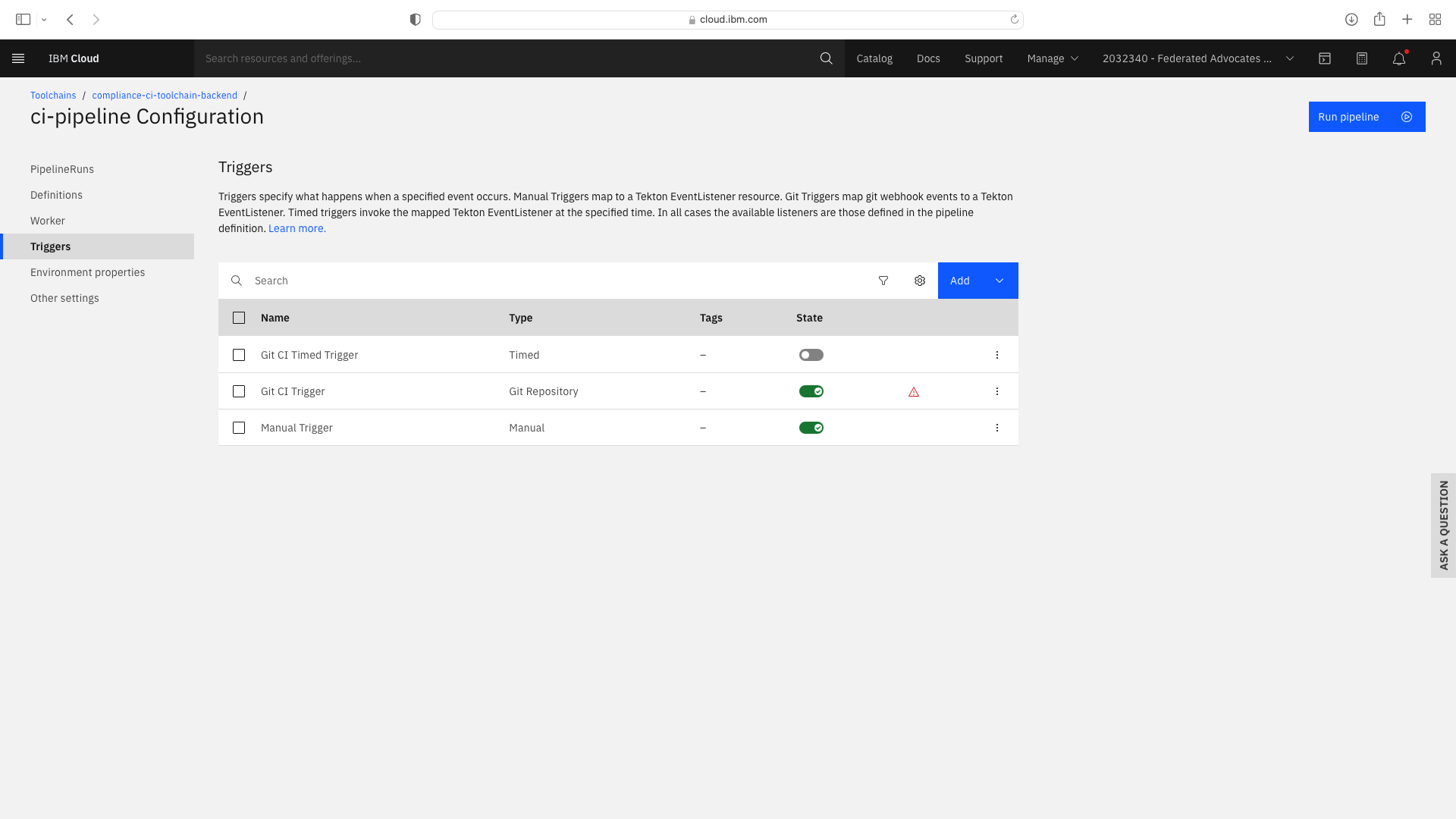
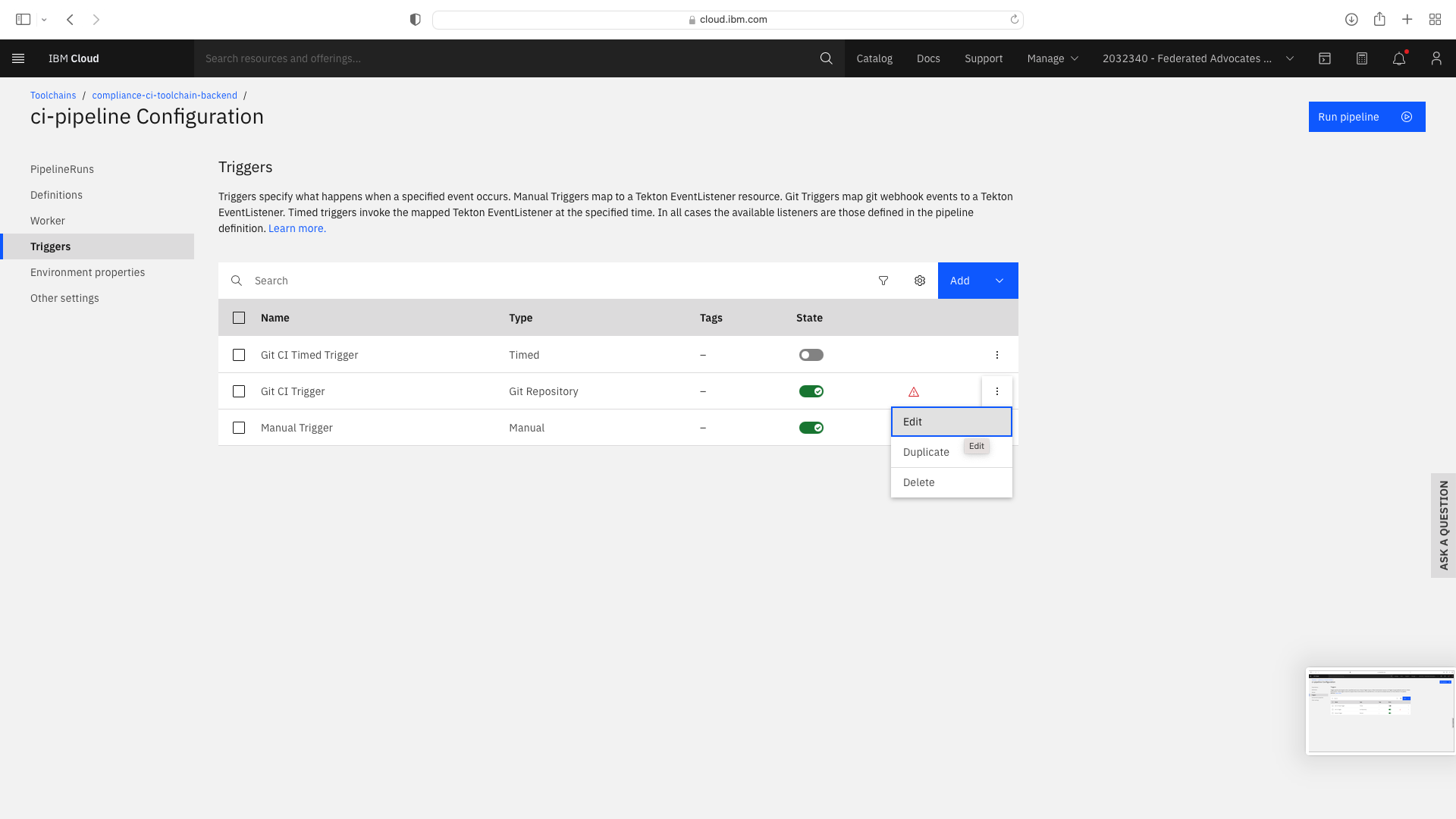
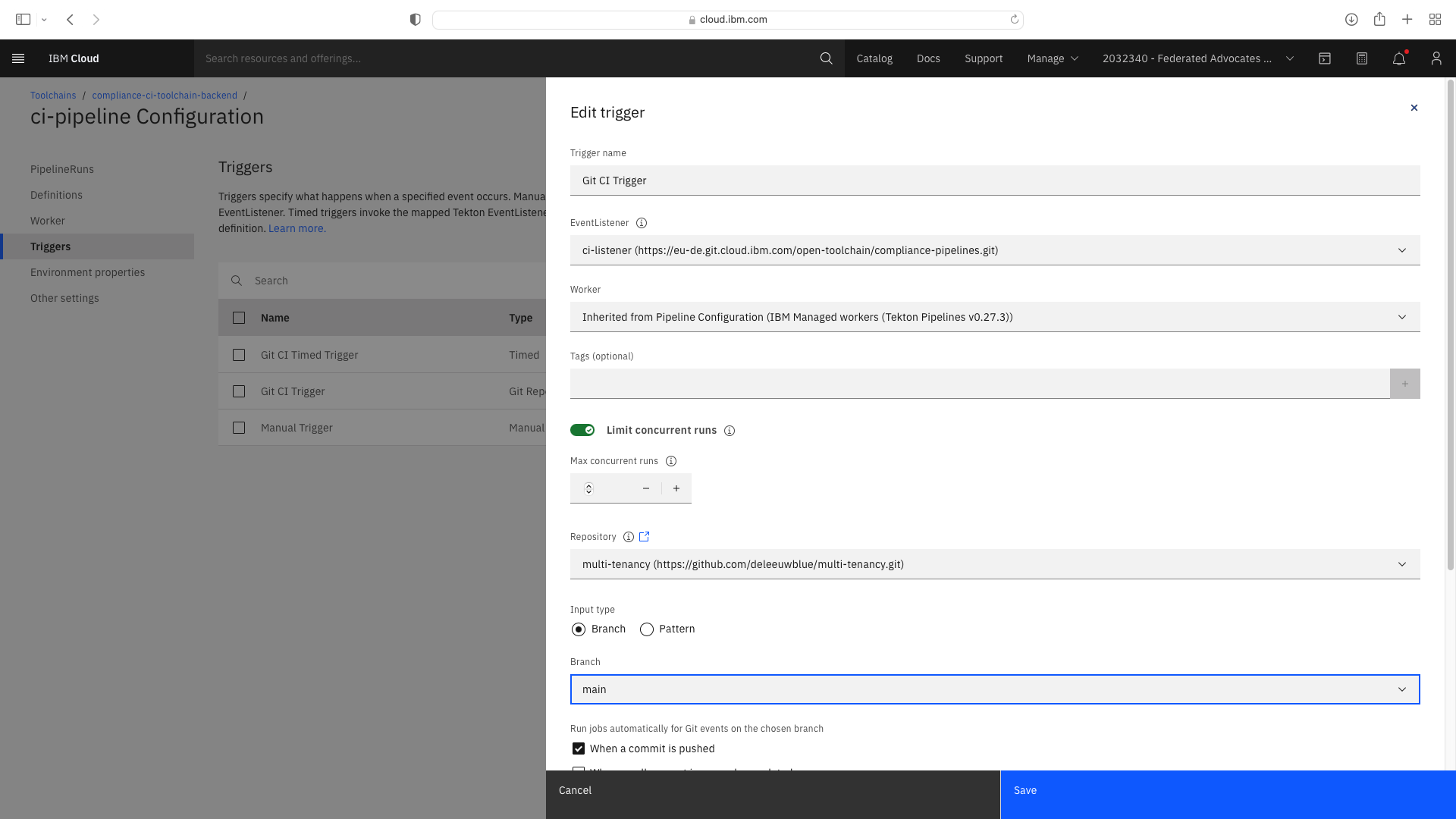
Create Dev Mode trigger & Update Environmental Properties for CI Frontend¶
Enable a Dev mode trigger which permits a faster pipeline run which does not invoke all compliance steps. Select the CI pipeline tile, then Trigger. Duplicate the existing Manual Trigger and set the properties as follows:
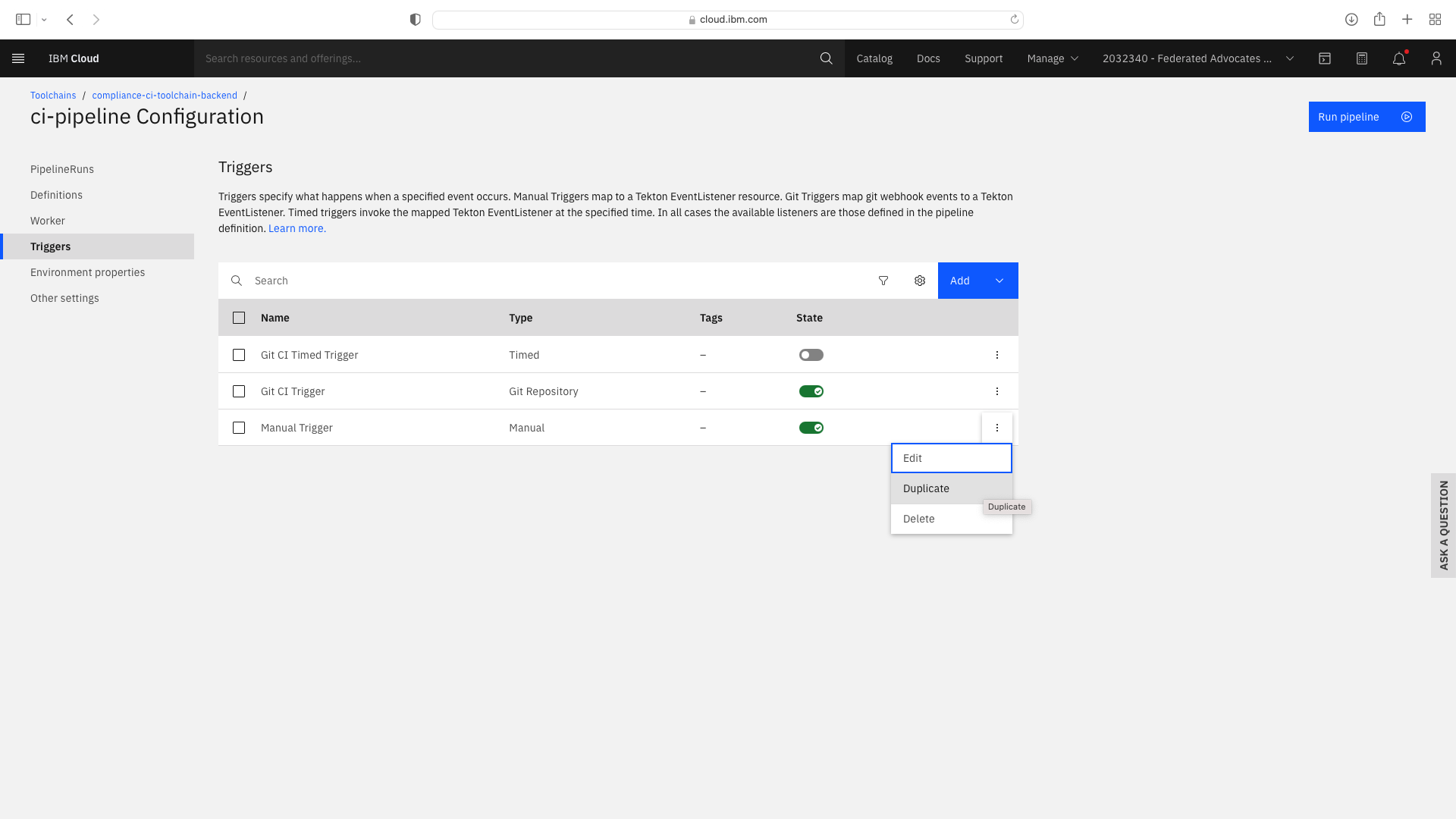
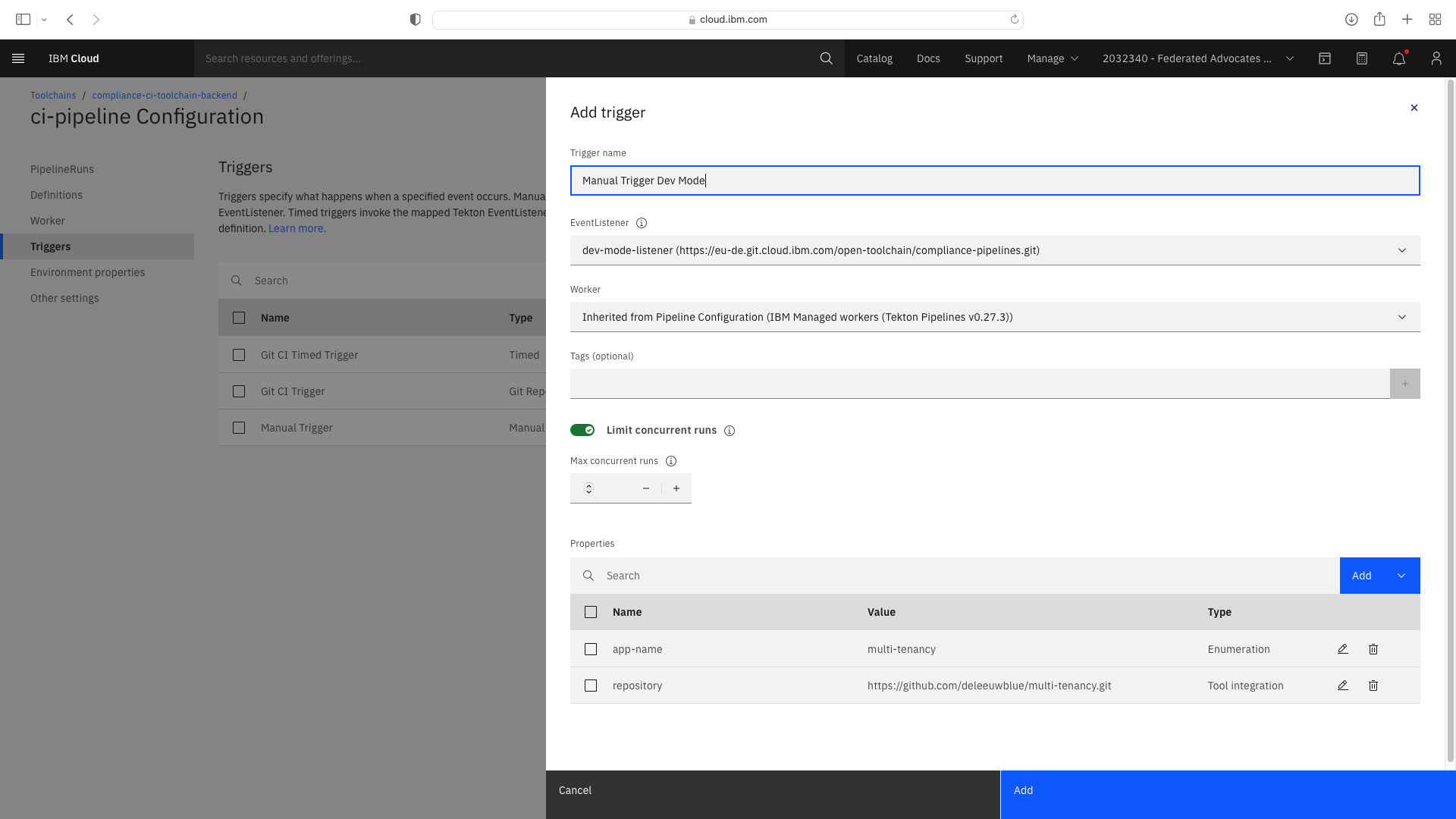
Add or update the Environmental Properties as follows:
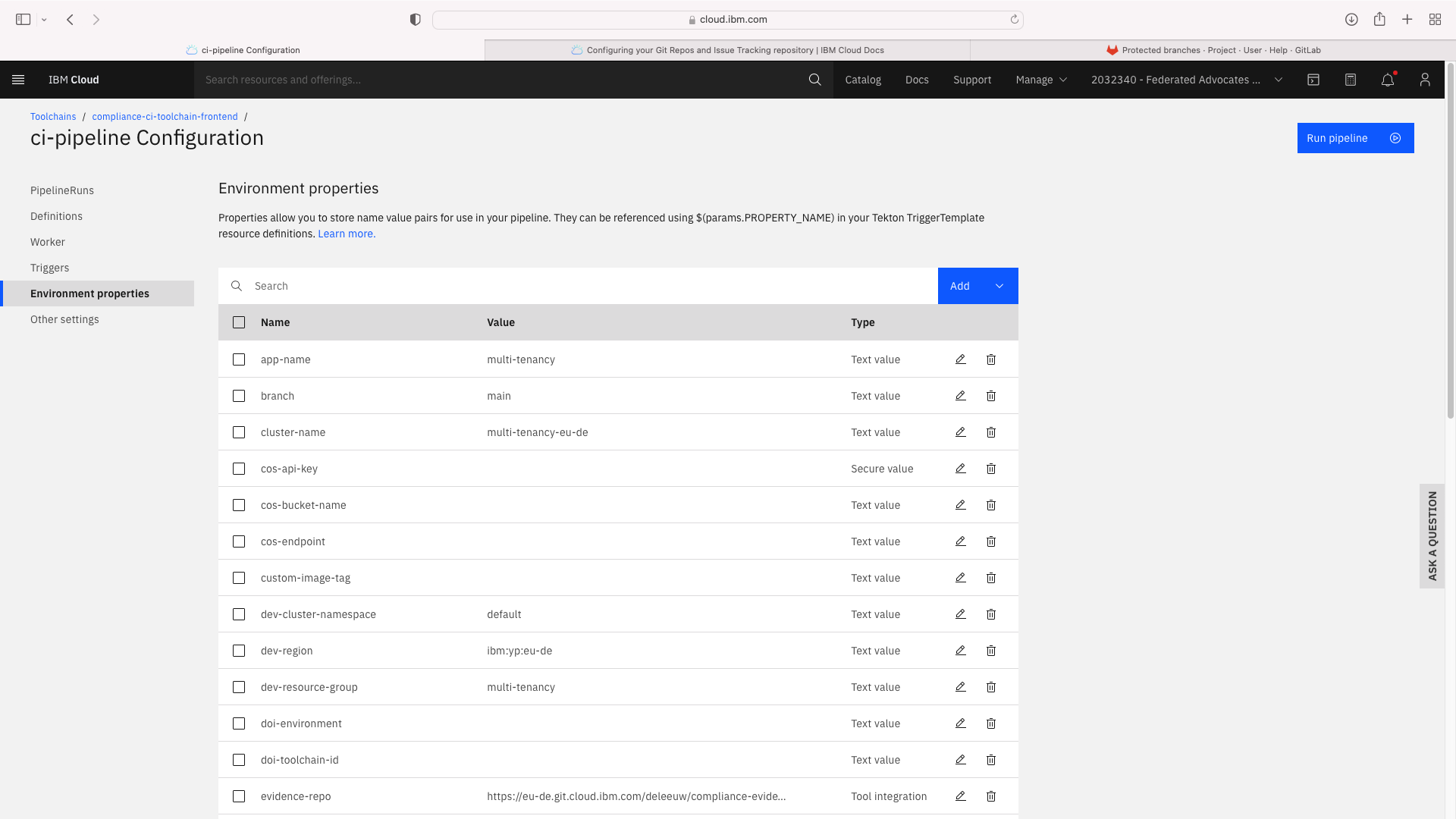
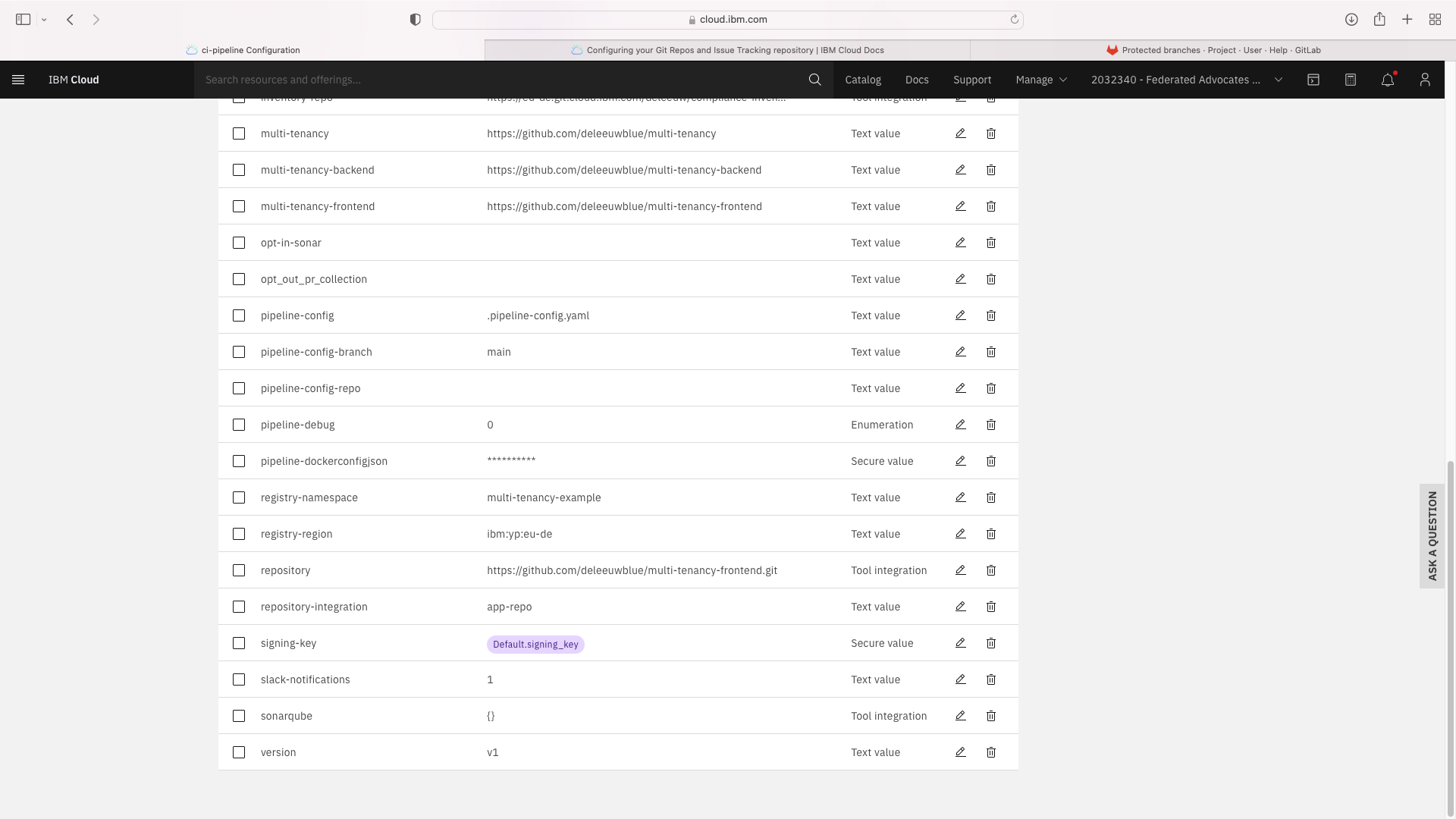
Note that the Text fields pipeline-config-branch and opt-in-sonar were updated.
Additional Text Fields entitled branch, multi-tenancy-frontend, multi-tenancy-backend and multi-tenancy were added.
An additional Tool Integration field entitled repository was added. When setting this field, you must specify a JSON filter of parameters.repo_url:
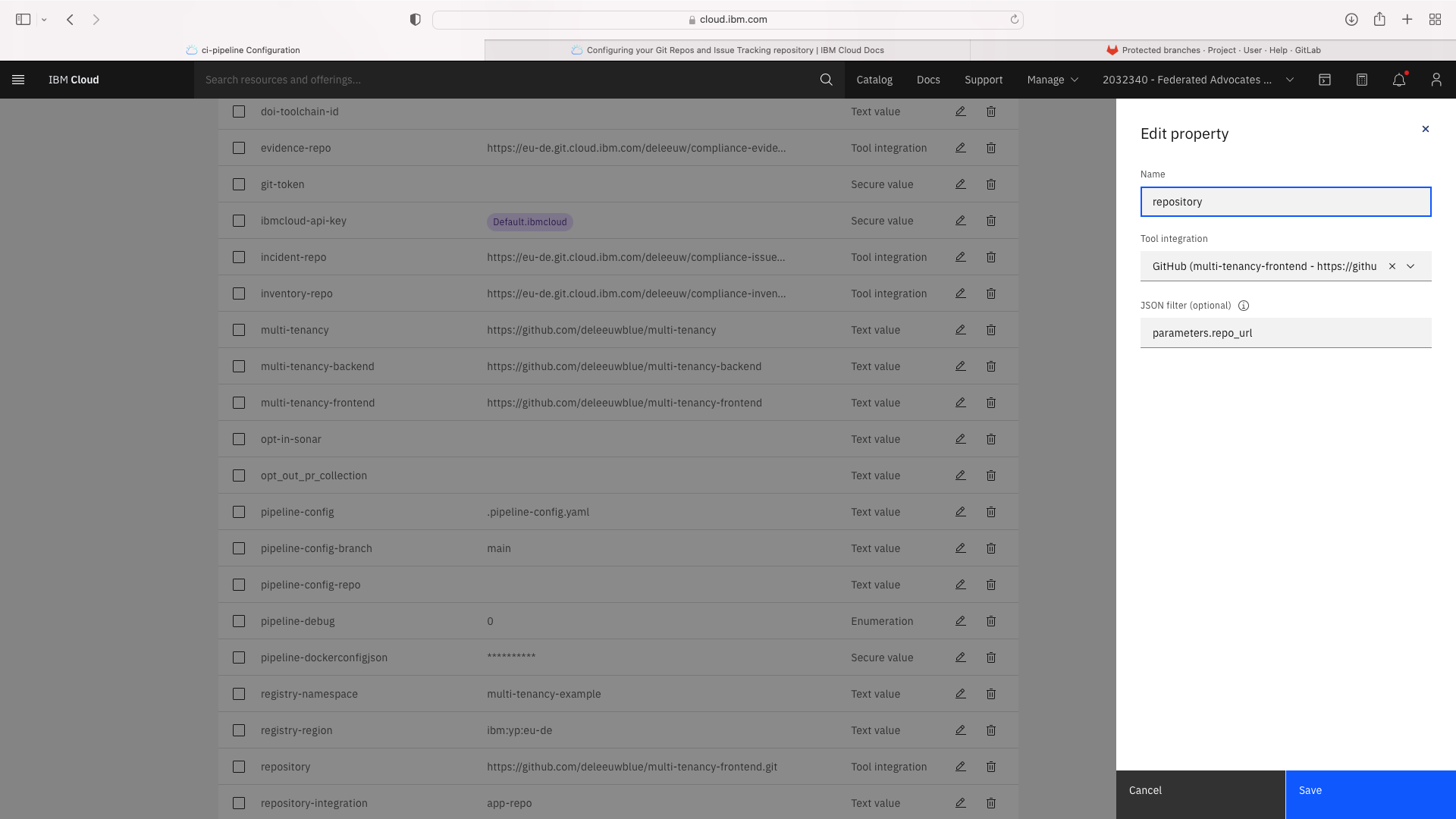
Select the Trigger tab. Note the Git CI Trigger shows a hazard symbol. Edit its properties and select a valid the branch name:
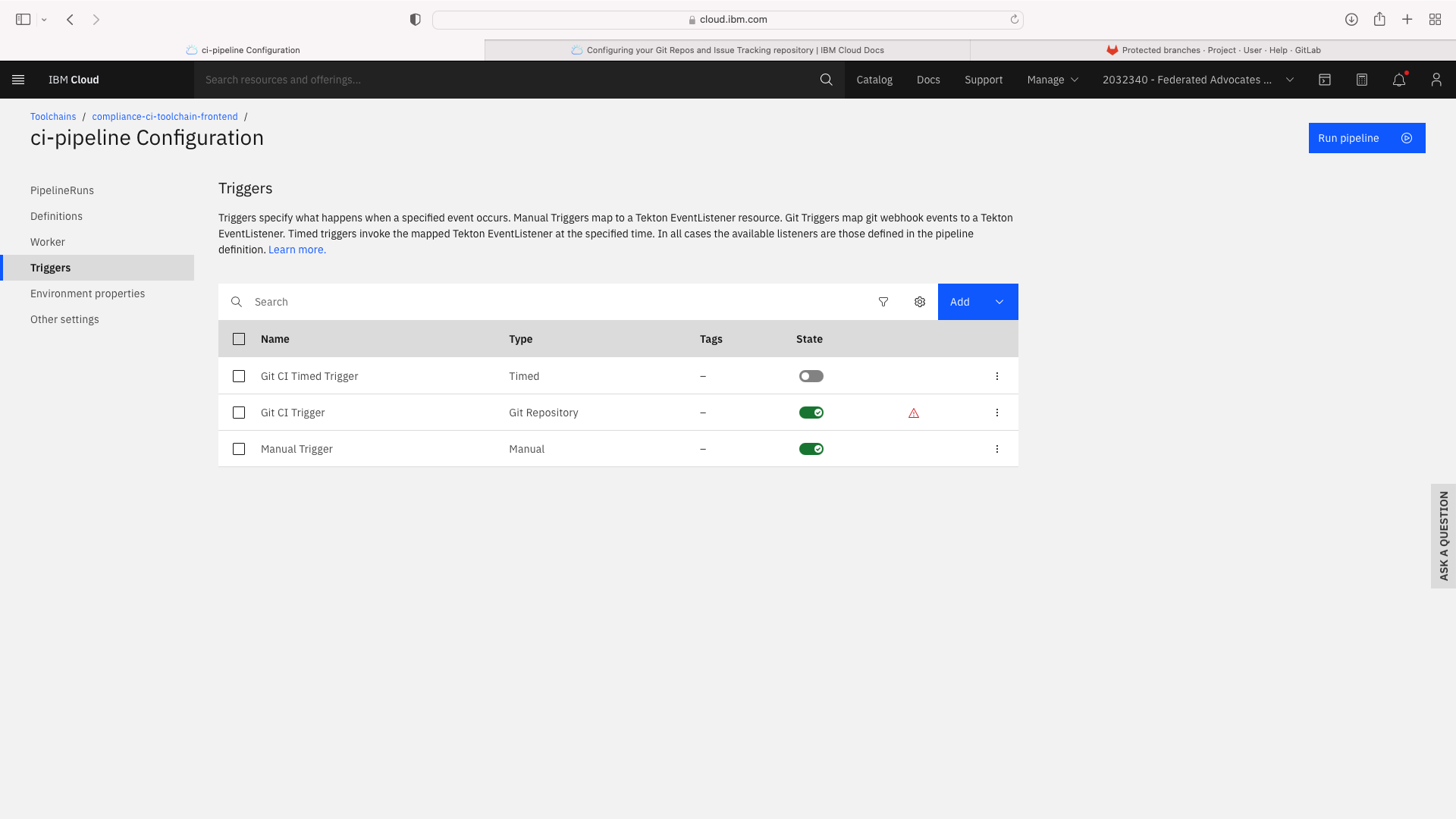
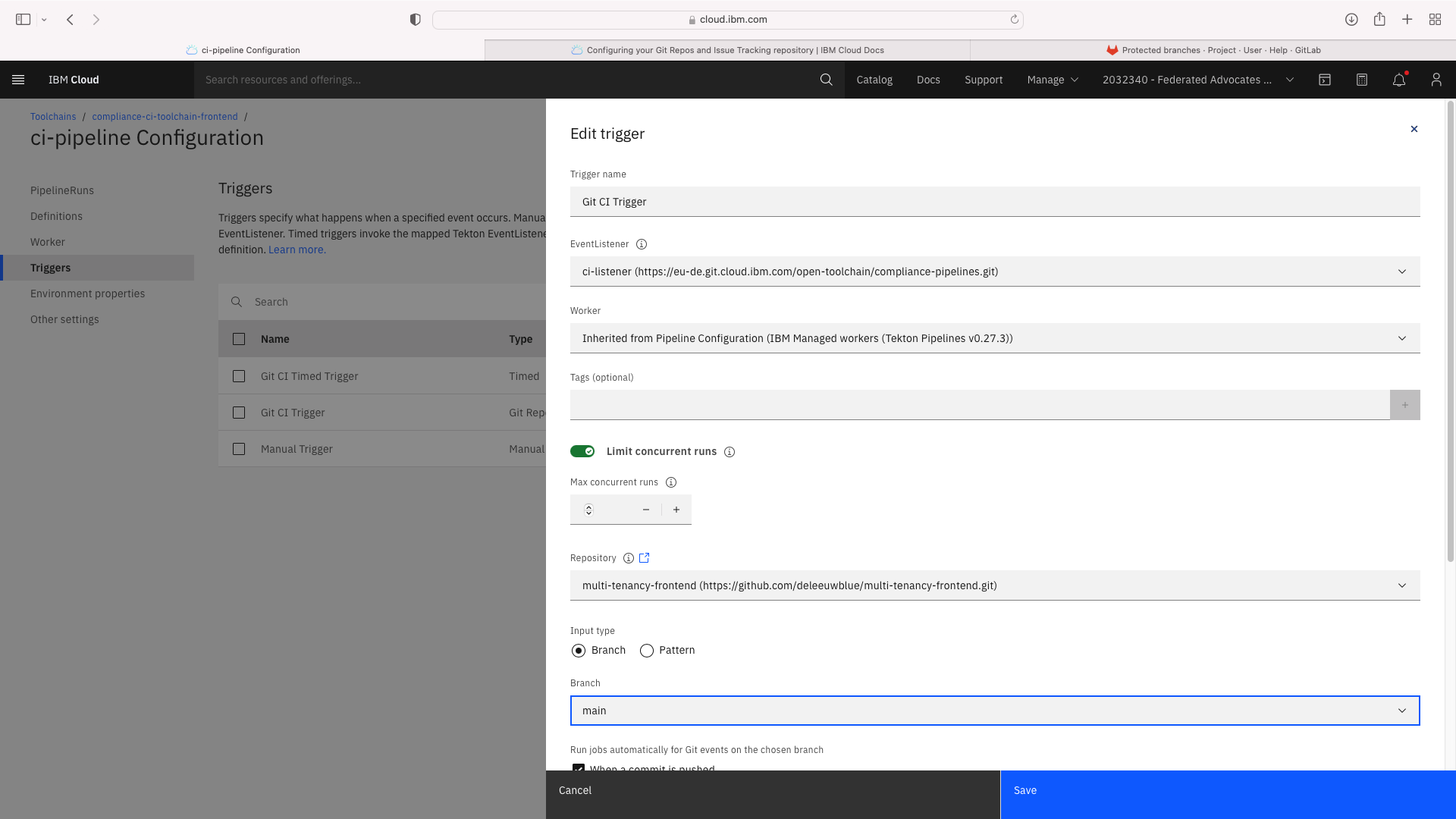
Create CI toolchain for frontend¶
Login to IBM Cloud and use the hamburger menu in the top left to navigate to DevOps. Select the Resource Group and Region thenh Create Toolchain and select the DevSecOps filter:

Click the CI tile to launch the setup wizard, and complete the fields by refering to the following screenshots (refering to your own GitHub repos):
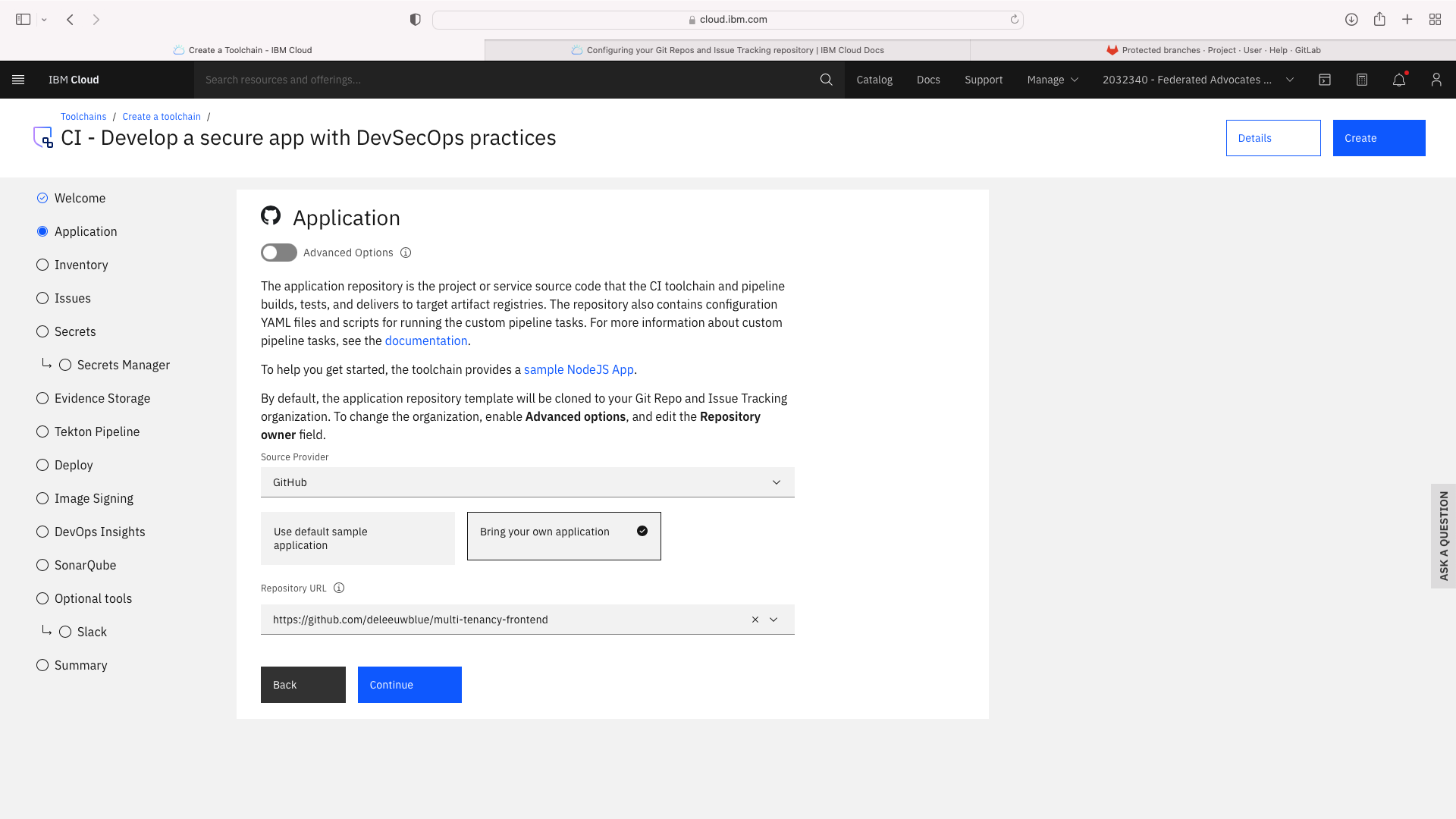
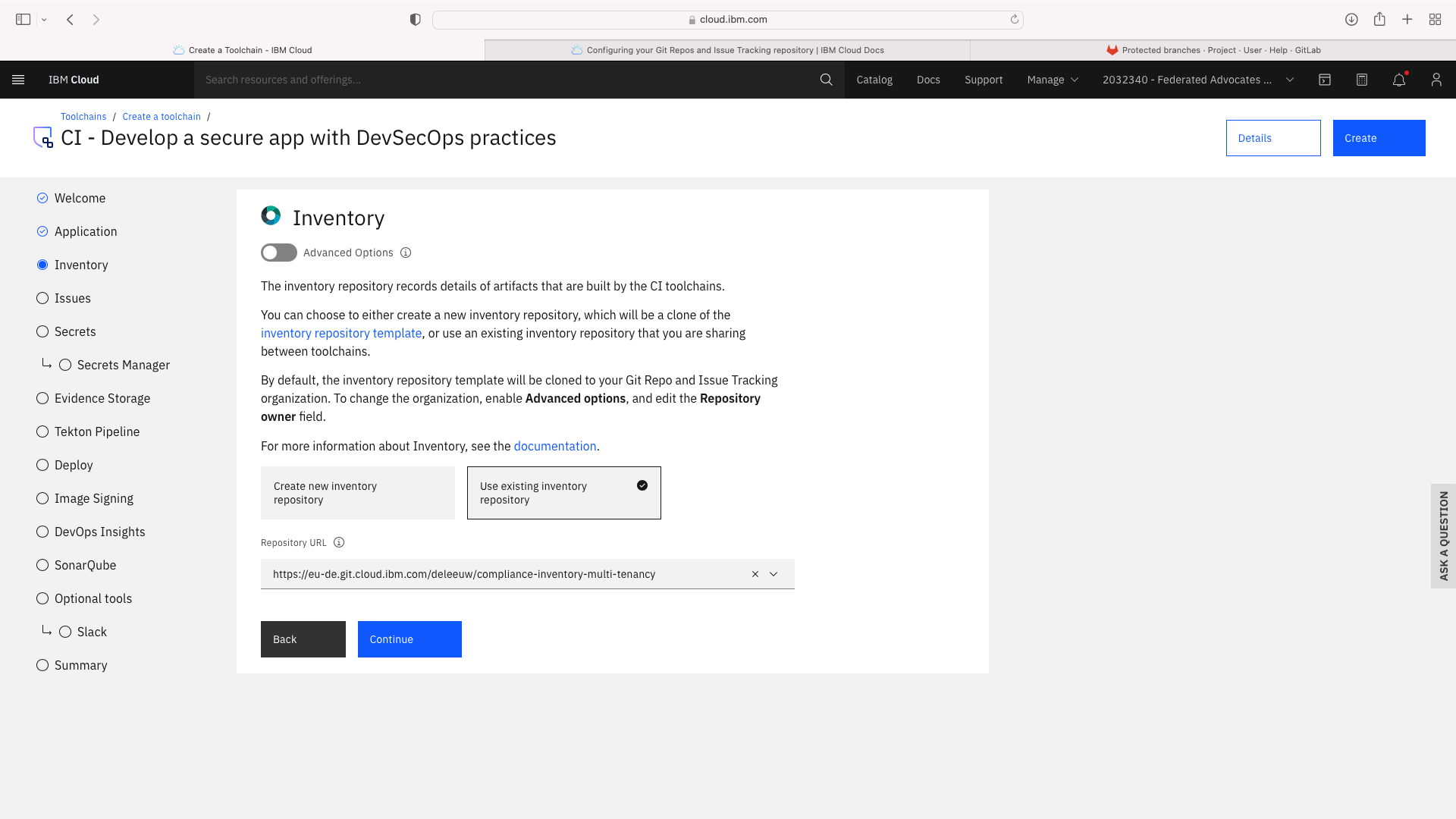
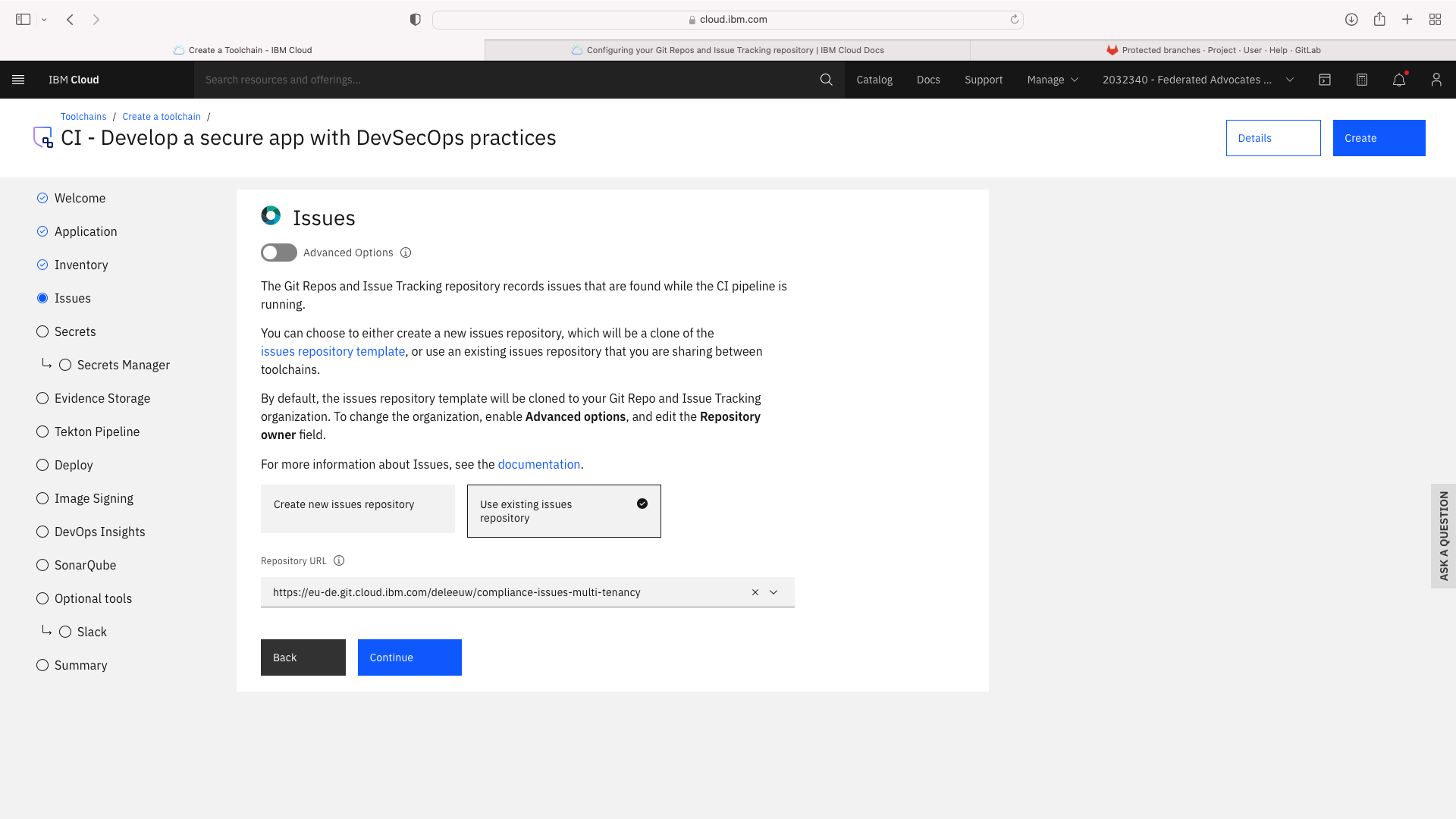
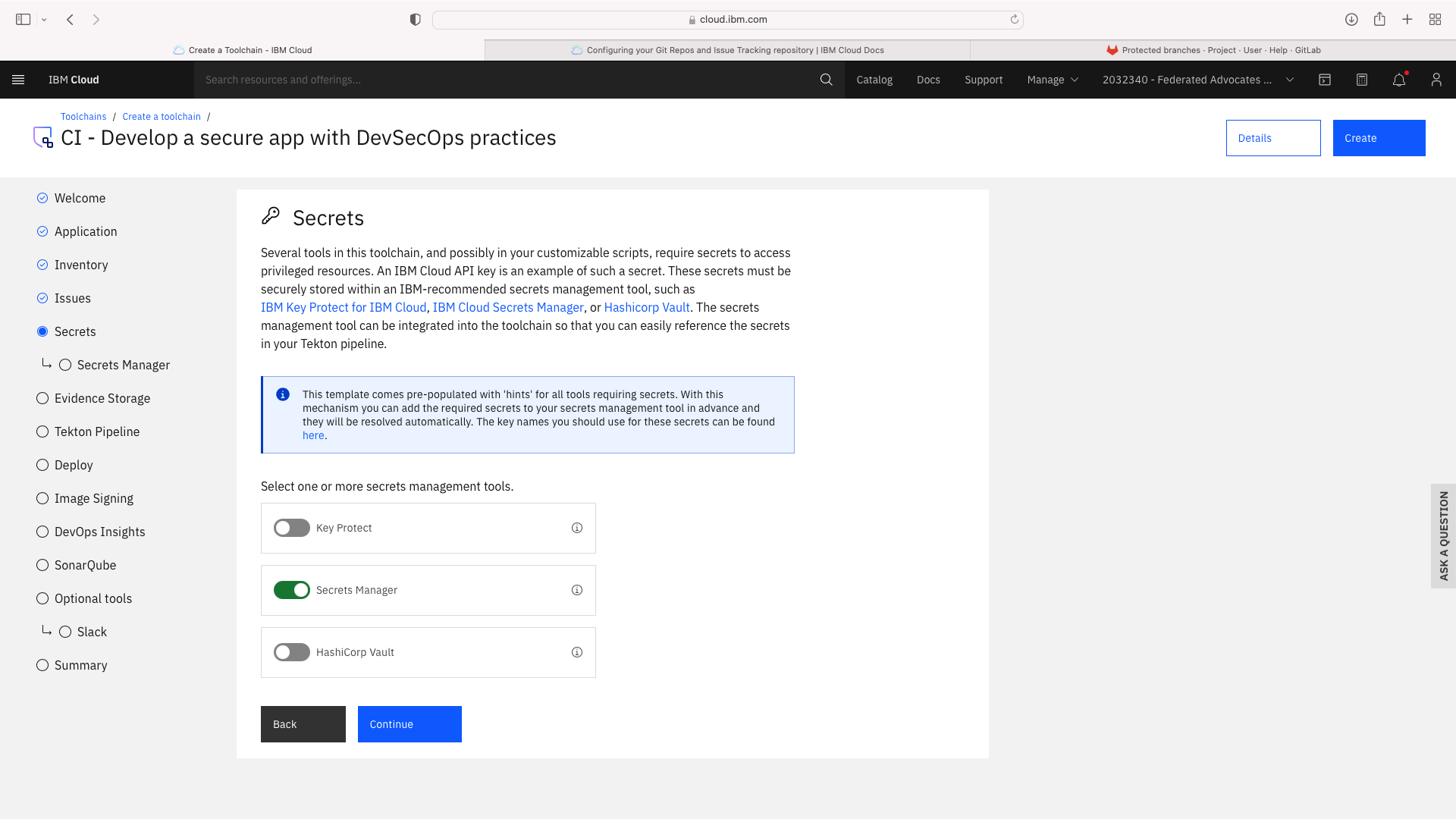
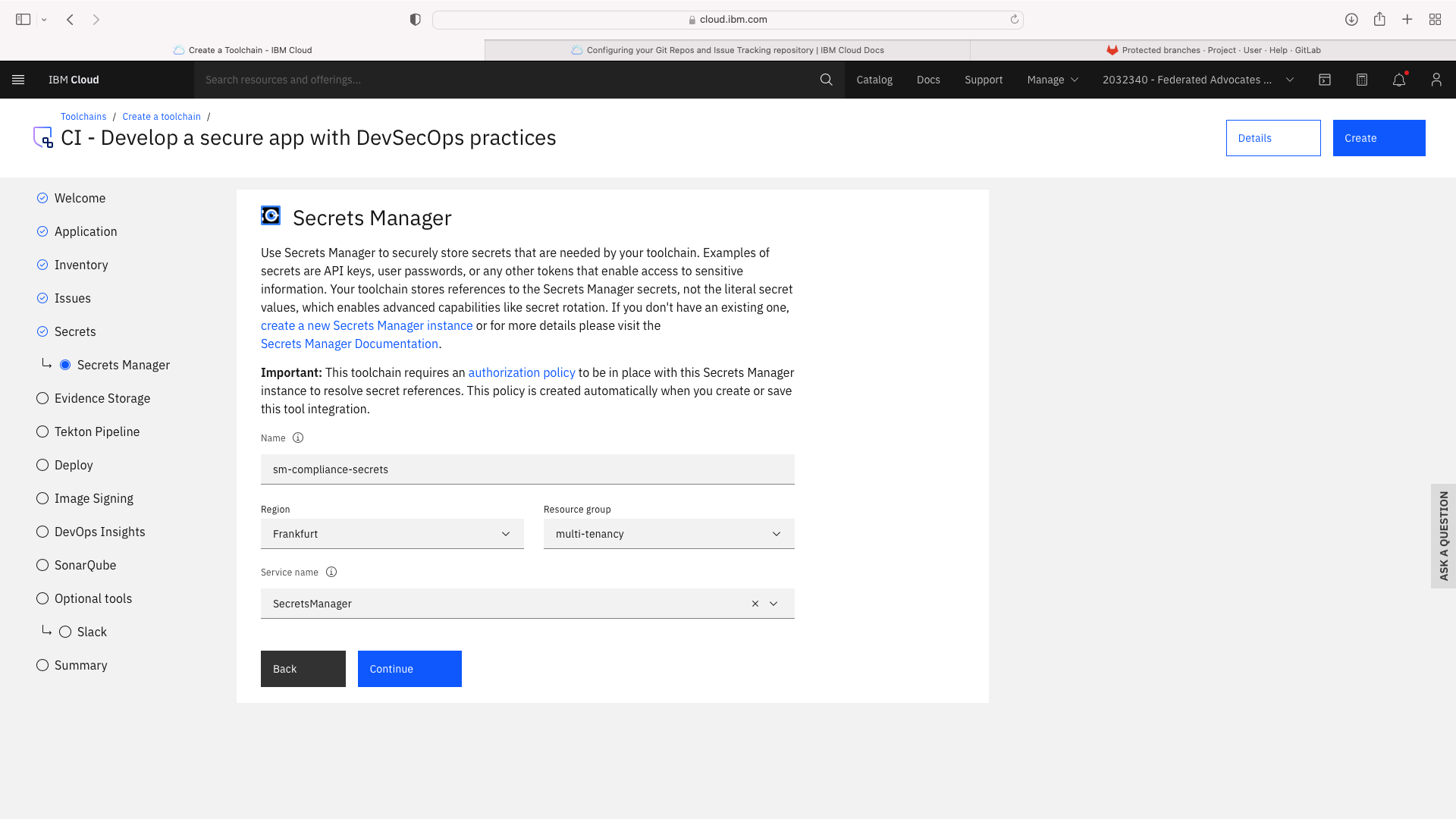
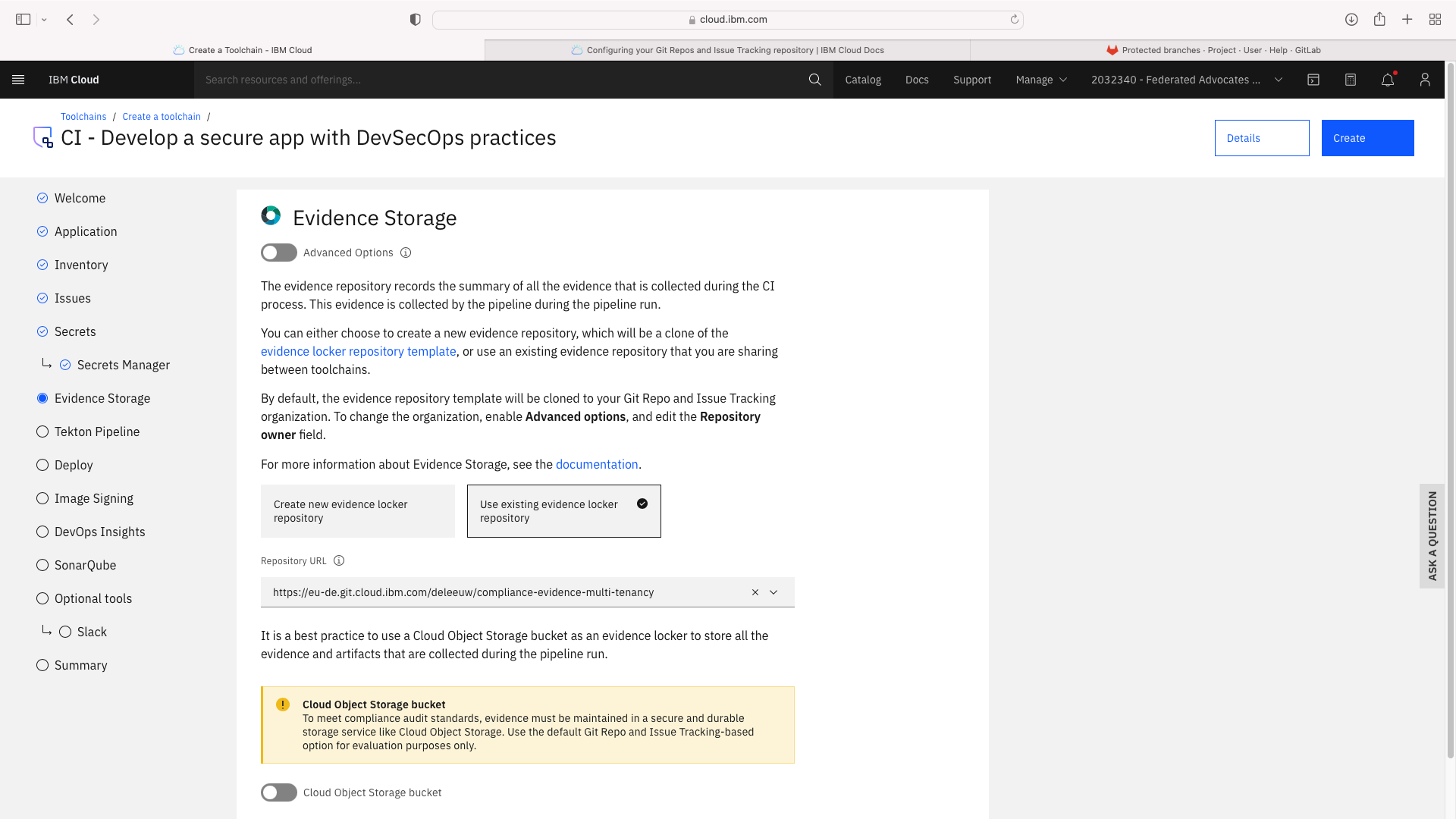
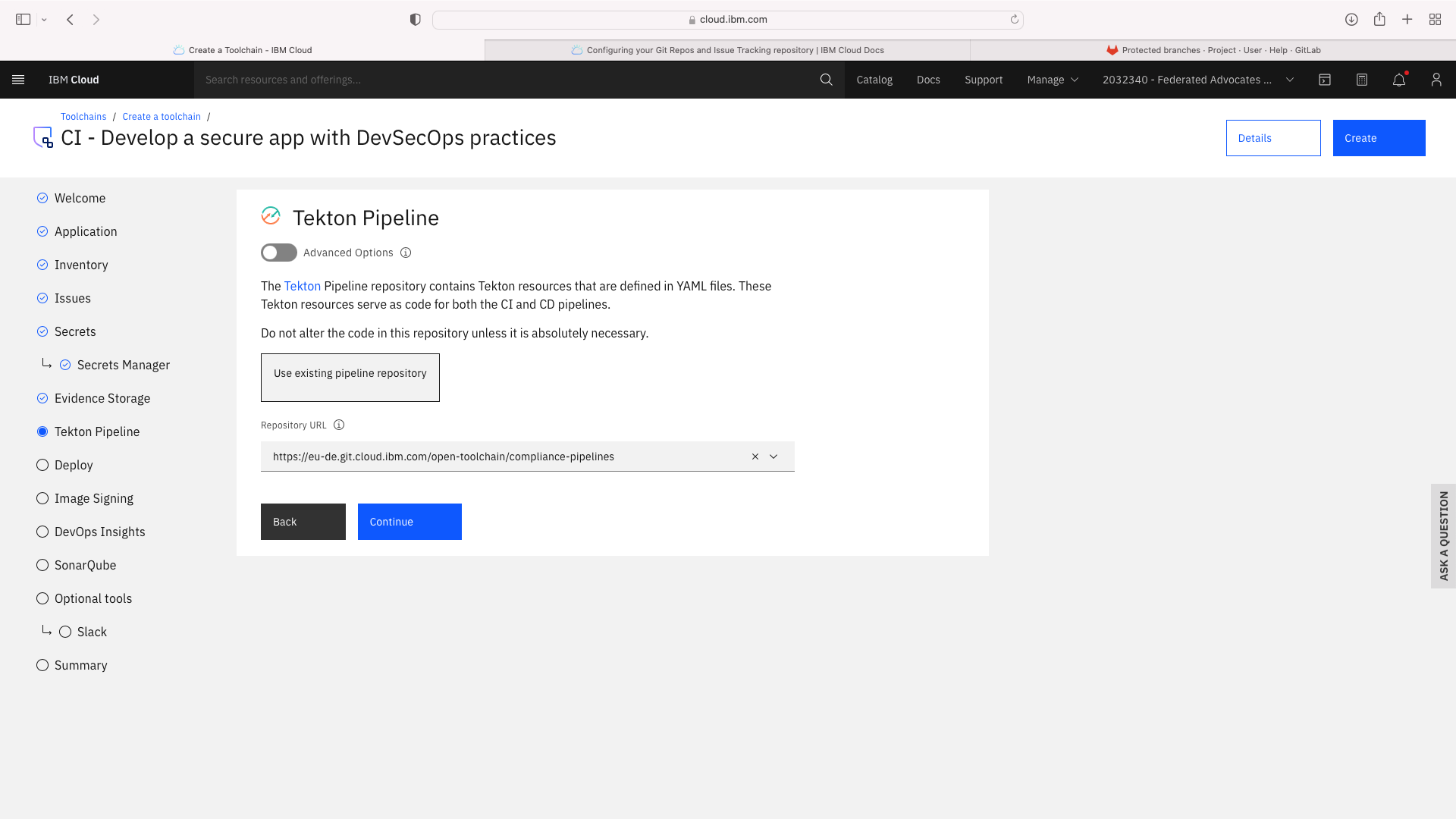
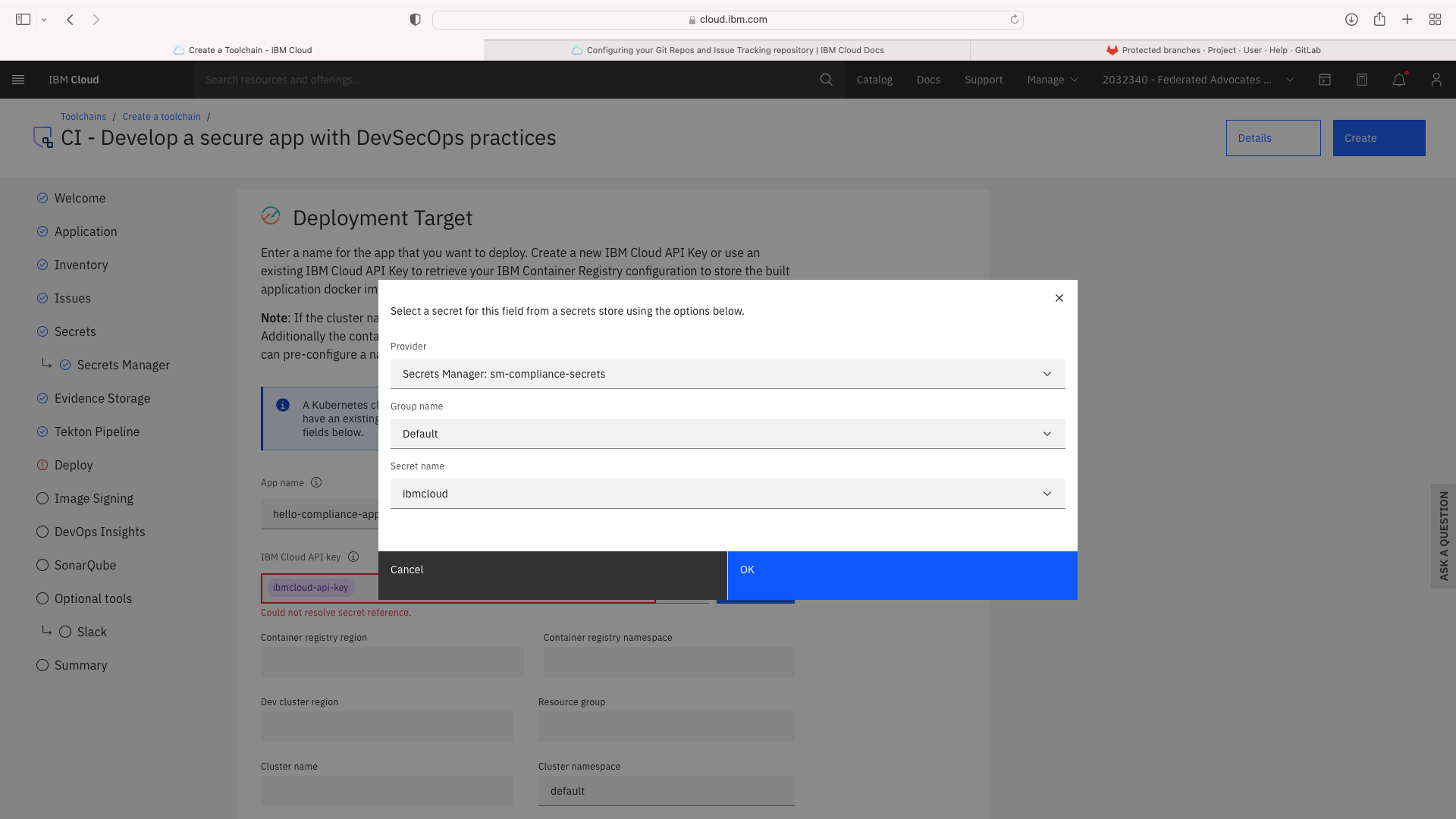
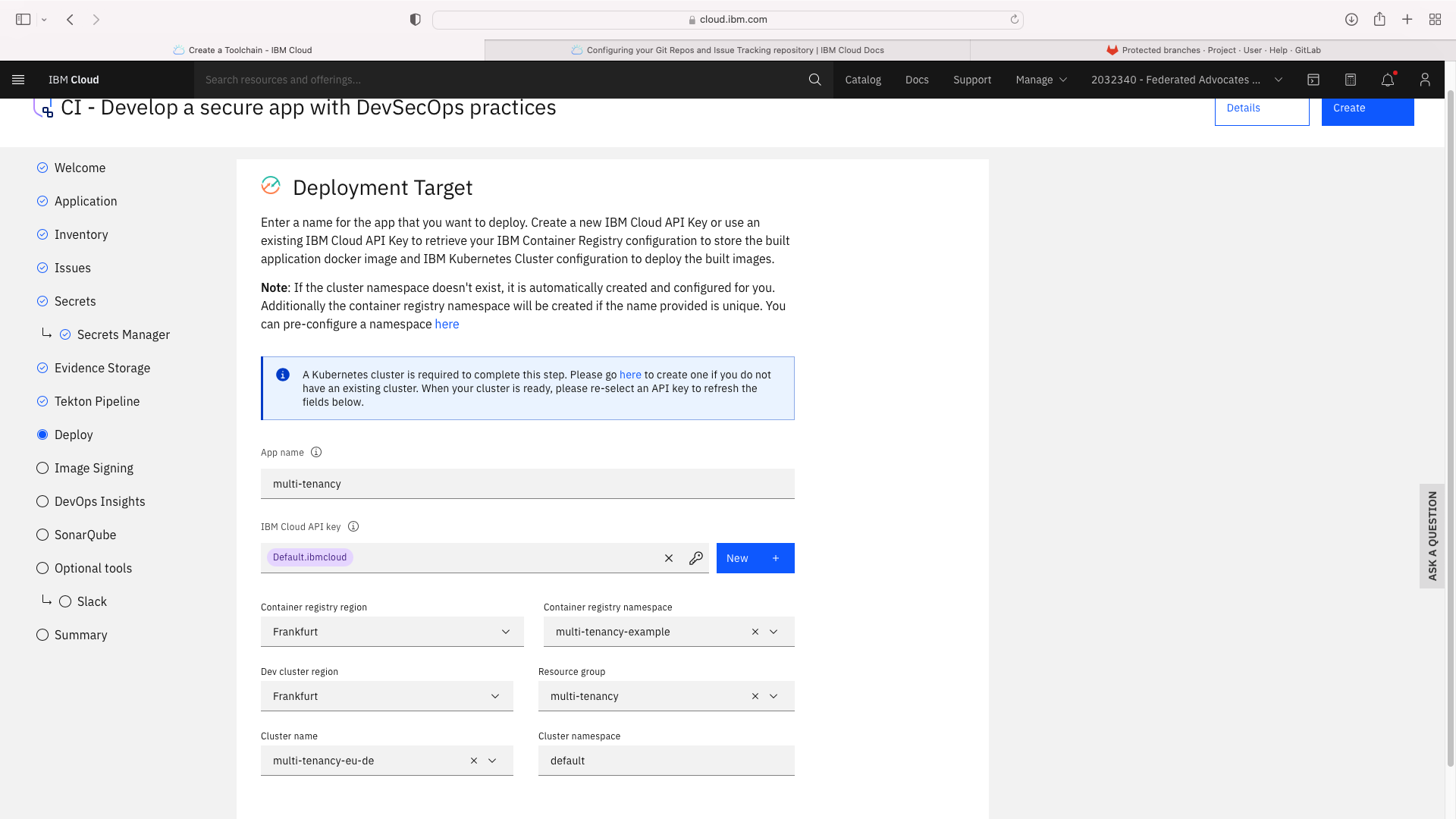
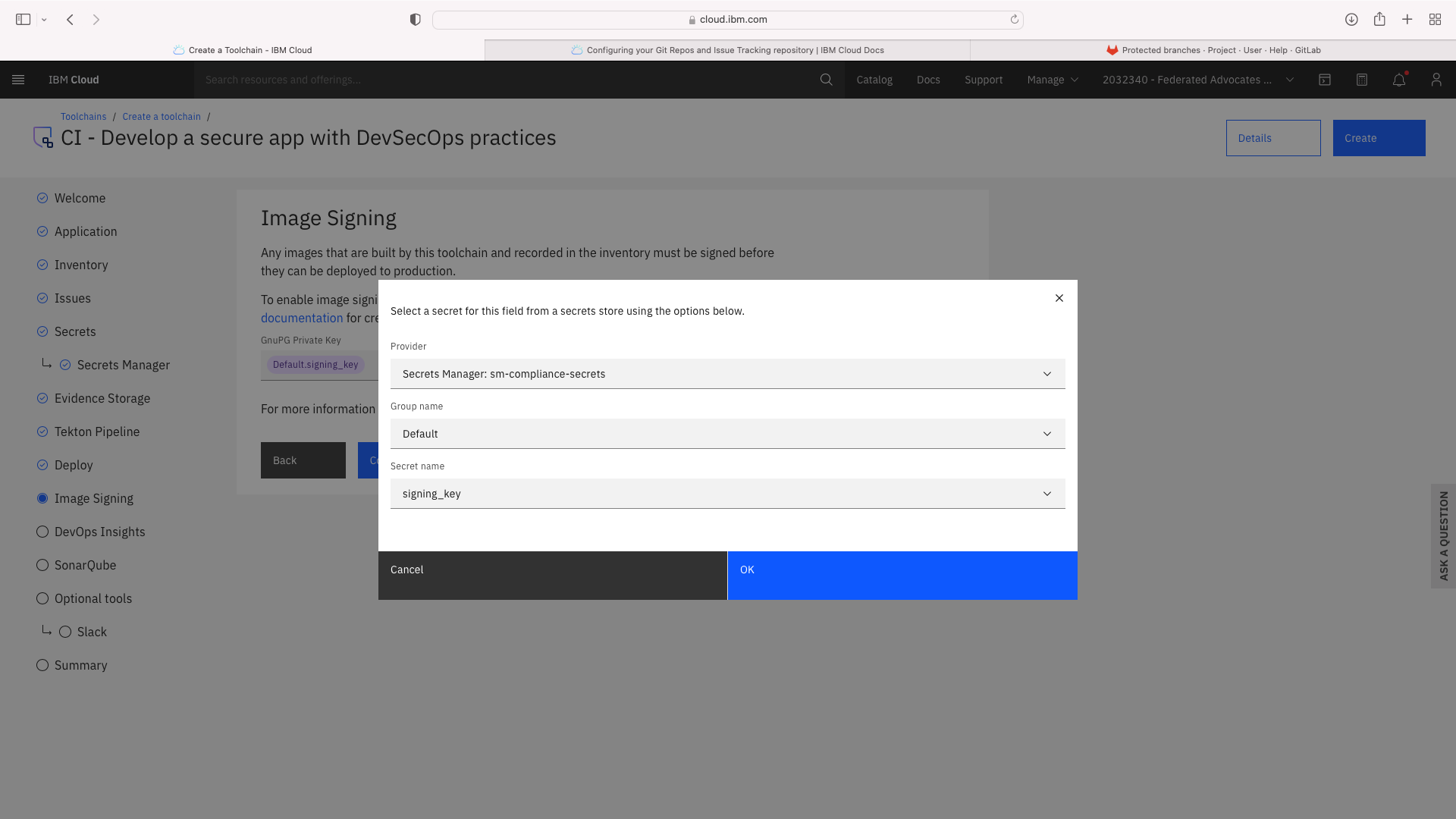
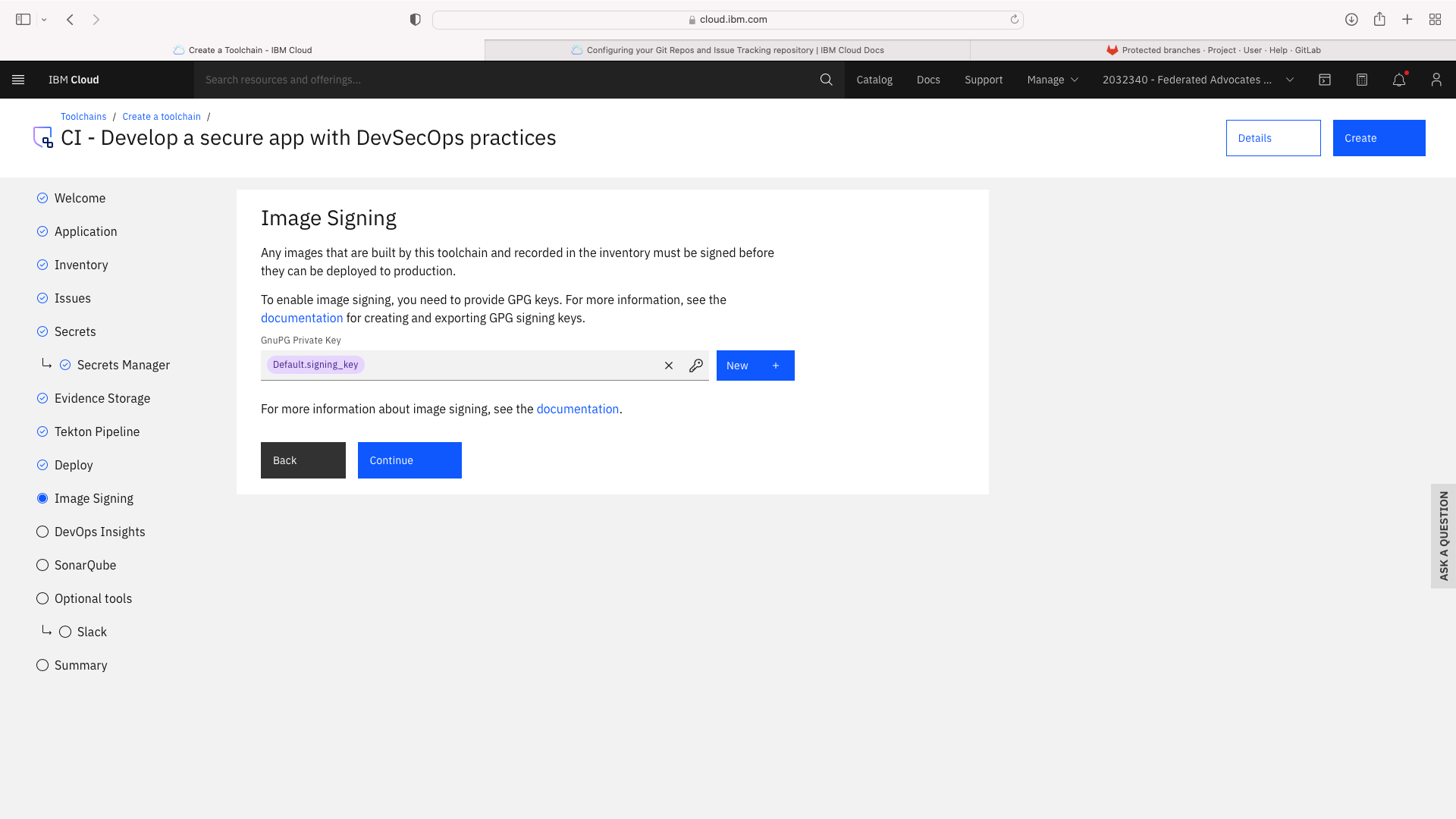
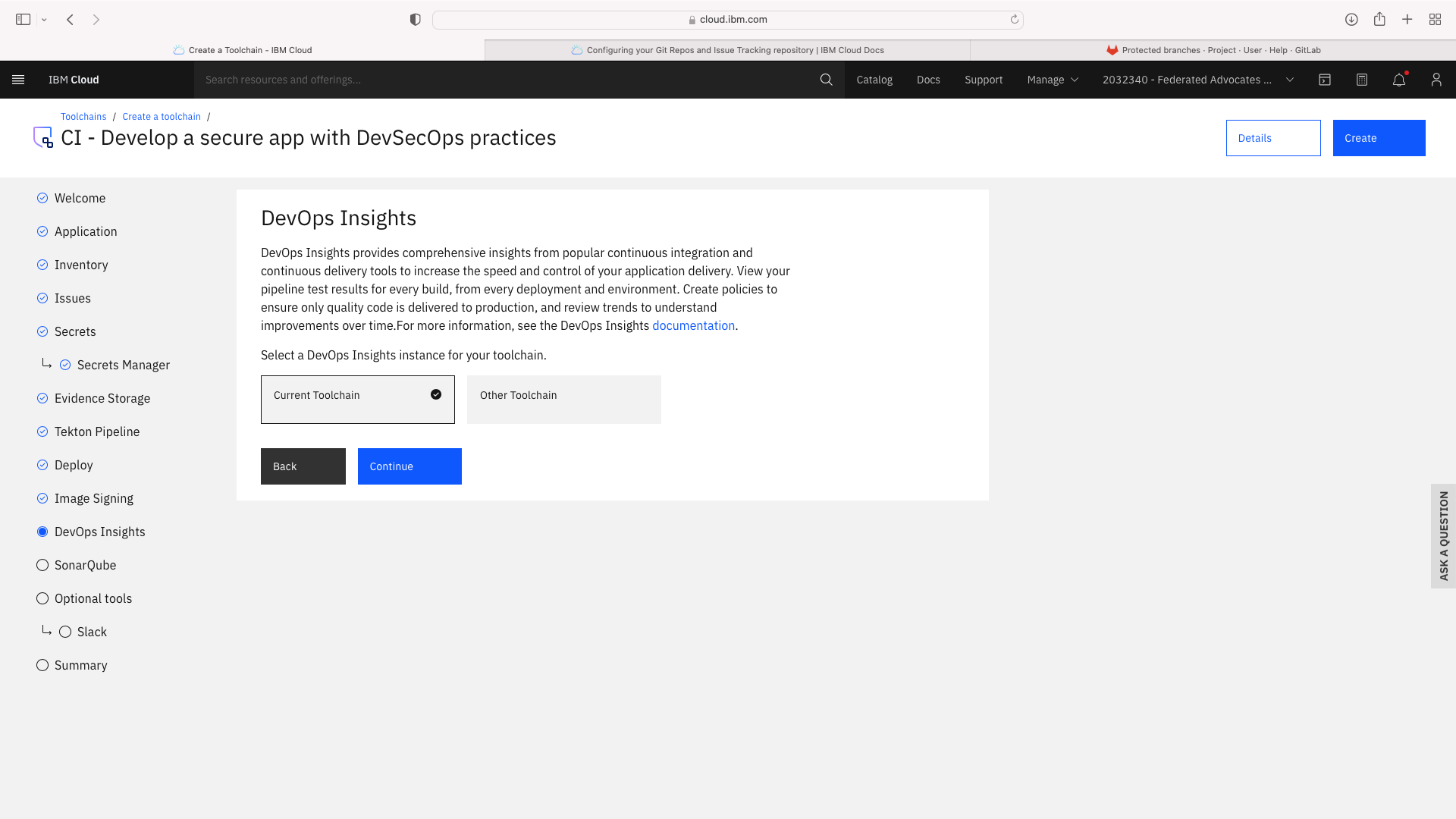
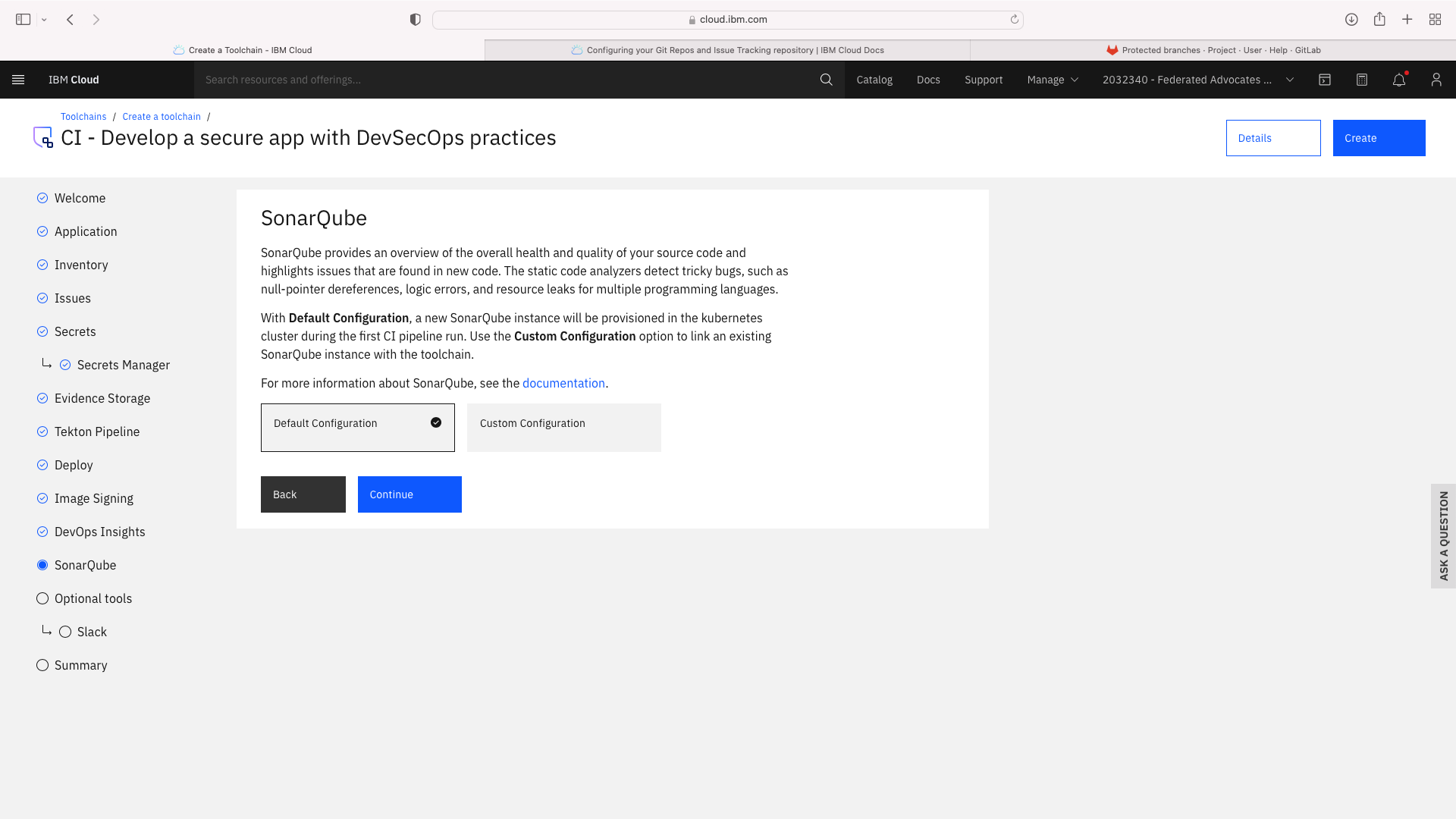
The CI pipeline for frontend also requires access to the multi-tenancy repostory, in addition to the multi-tenancy-backend repostory which has already been configured by the wizard. Click the blue Add tool button and manually add the GitHub repostory for multi-tenancy by following these steps:
Create Dev Mode trigger & Update Environmental Properties for CI Backend¶
Enable a Dev mode trigger which permits a faster pipeline run which does not invoke all compliance steps. Select the CI pipeline tile, then Trigger. Duplicate the existing Manual Trigger and set the properties as follows:

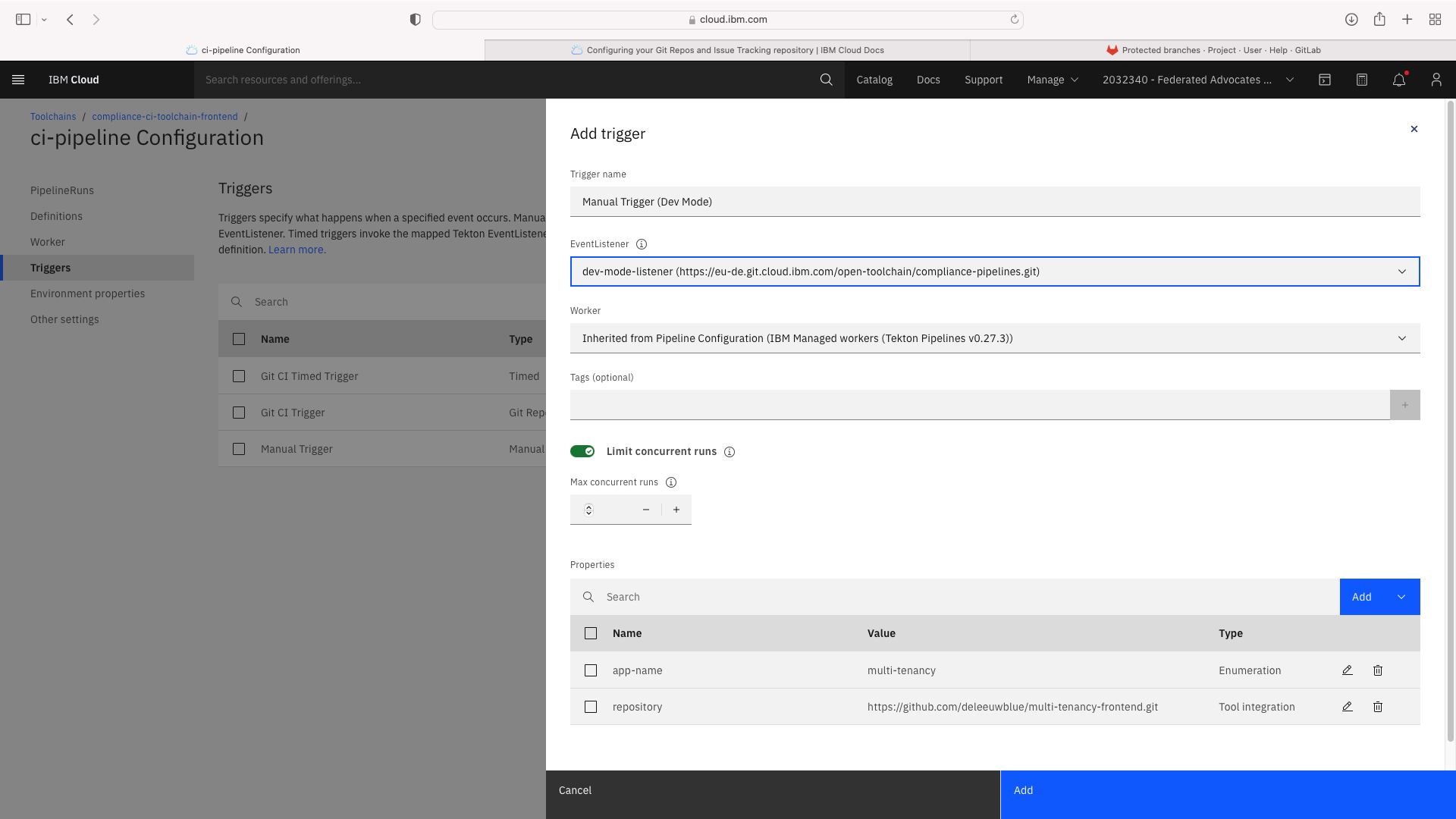
Add or update the toolchain's Environmental Properties as follows:


Note that the Text fields pipeline-config-branch and opt-in-sonar need to be modified.
An additional Text Fields entitled branch, multi-tenancy-frontend, multi-tenancy-backend and multi-tenancy were added.
An additional Tool Integration field entitled repository was added. When setting this field, you must specify a JSON filter of parameters.repo_url:

Select the Trigger tab. Note the Git CI Trigger shows a hazard symbol. Edit its properties and select a valid the branch name:


Testing the CI pipelines (Optional)¶
In this section, you can make a quick test of the CI pipelines. For a more detailed explanation of how to use the pipelines to onboard a new tenant, see the Overview section.
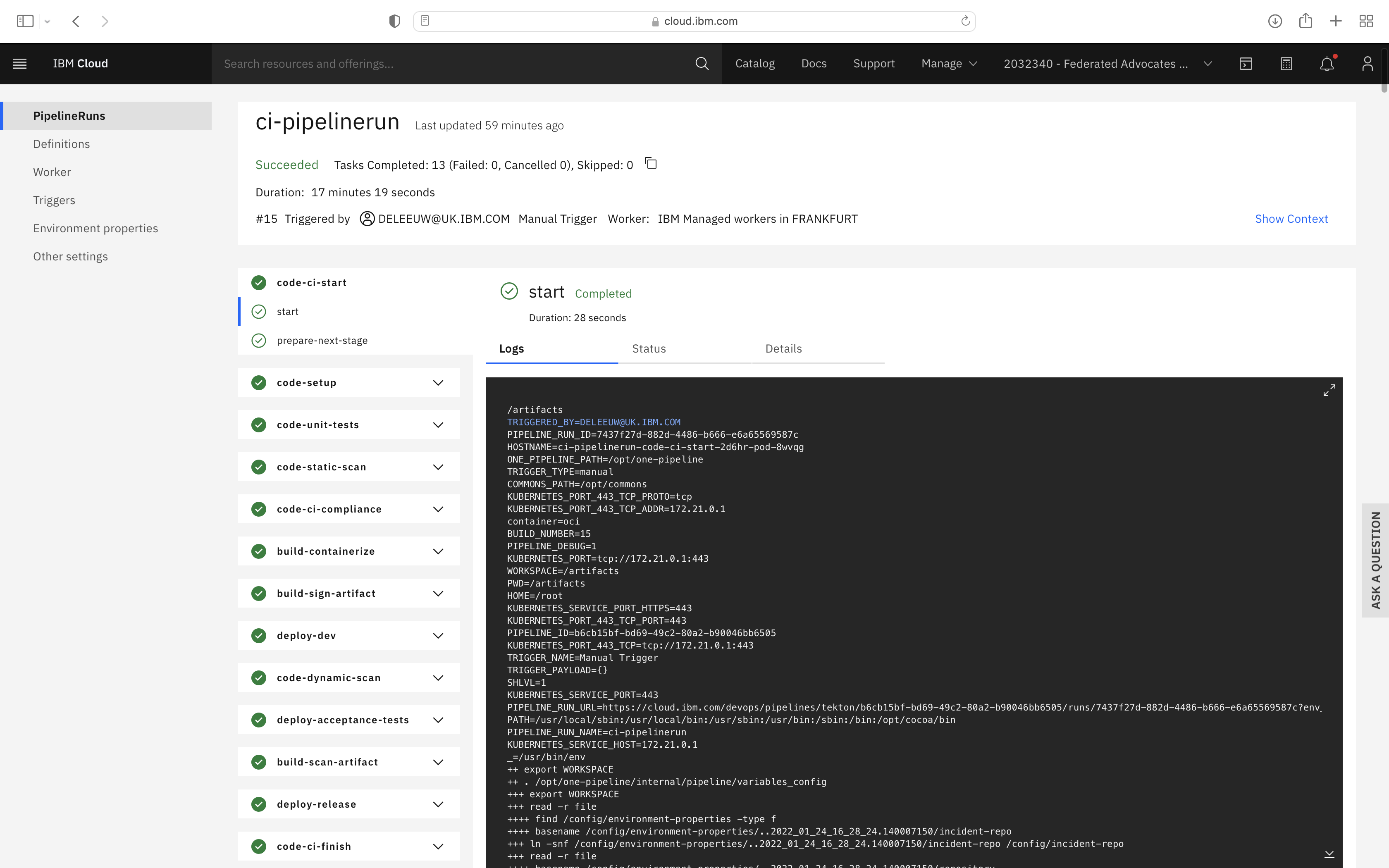
First test the backend CI pipelines by triggering a pipeline run, using Manual Trigger. Click the pipeline run name to view the progress. After a few minutes, a successful result should look like this:
Test the front end CI pipeline by triggering a pipeline run, using Manual Trigger. Click the pipeline run name to view the progress. After a few minutes, a successful result should look like this:
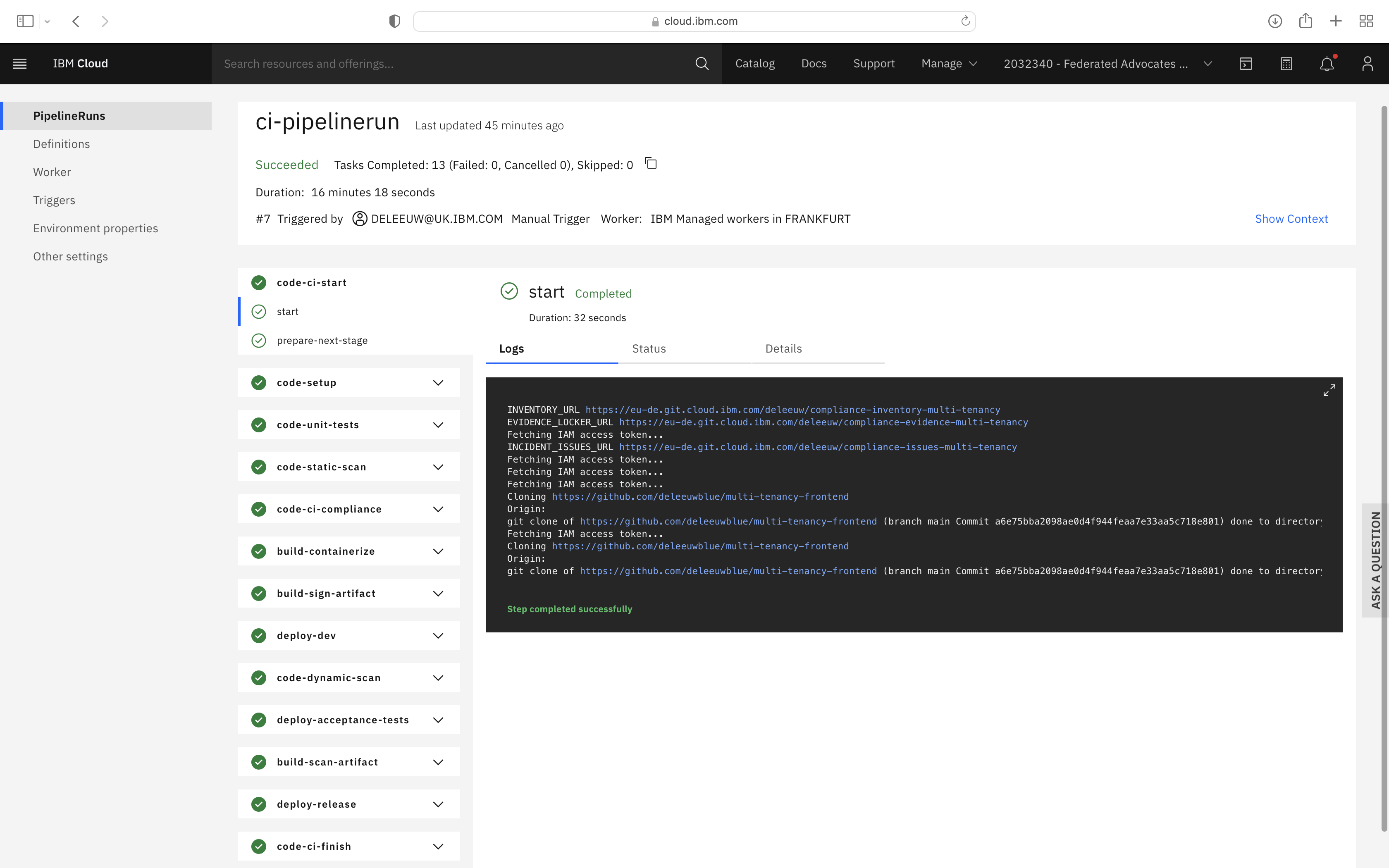
If all steps complete successfully, you can configure and test the CD Toolchain.